Has your WordPress website been hacked? Don’t worry! This comprehensive guide will help you to fix your site; if not, we can help you.
Did you know? Cybercrime costs 6 trillion dollars per year to companies. Businesses still don’t take WordPress security seriously until their websites get hacked.
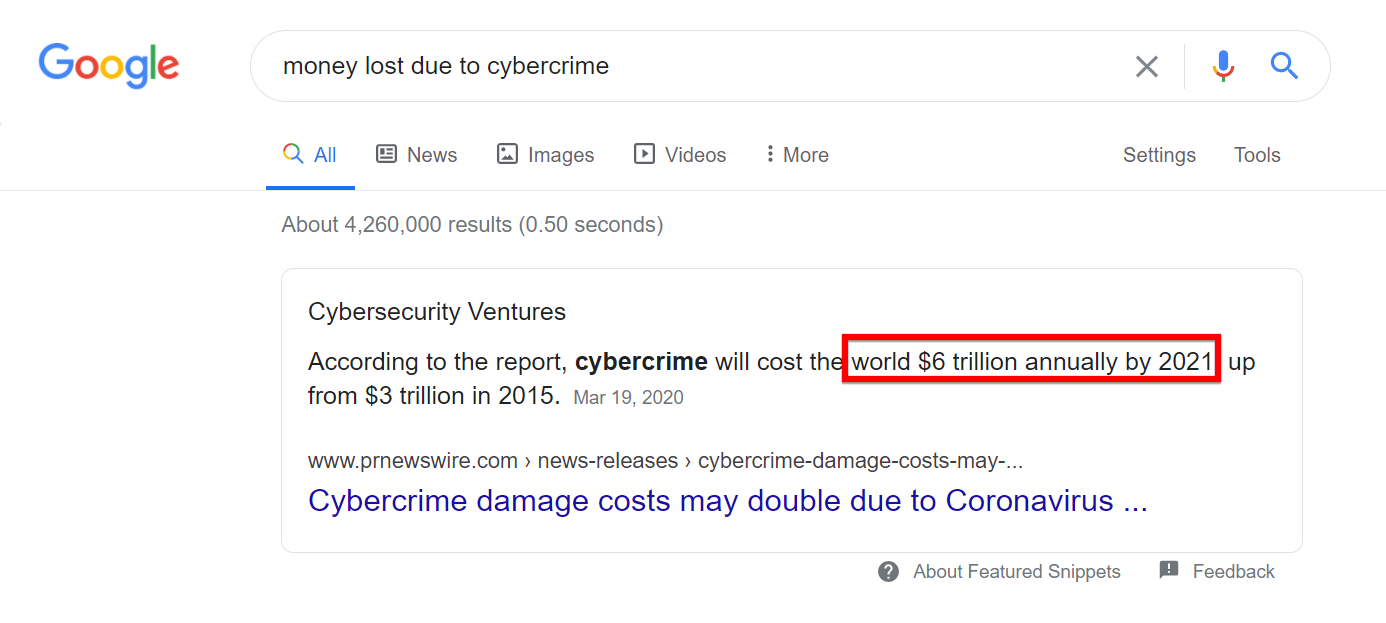
Table of Content
- 5 Steps to Fix a Hacked WordPress Website
- Why WordPress Gets Hacked?
- What Do WordPress Hacked Websites Look Like?
5 Steps to Fix a Hacked WordPress Website
Fixing a hacked WordPress website is a step by step process. Follow the steps:
Step 1: Stay Calm
Most people get panic attacks when their websites get hacked. Being scared would hinder the mental and emotional system of your brain. Take deep breaths to get more oxygen since breathing is the most effective technique for reducing anxiety quickly. Challenge your thoughts by questioning and answering:
- Will I lose money? Yes, you’ll lose some money, but it’s temporary. You can recover from it.
- What is the worst that could happen? If domain and hosting are on your name, you don’t need to worry about it.
- Does my hosting provide support? If your hosting takes daily backups and offers a free hack-fix guarantee, just send them a message.
Step 2: Change Passwords and Salt Changes
If a hacker has compromised WordPress, you should immediately change all your passwords of:
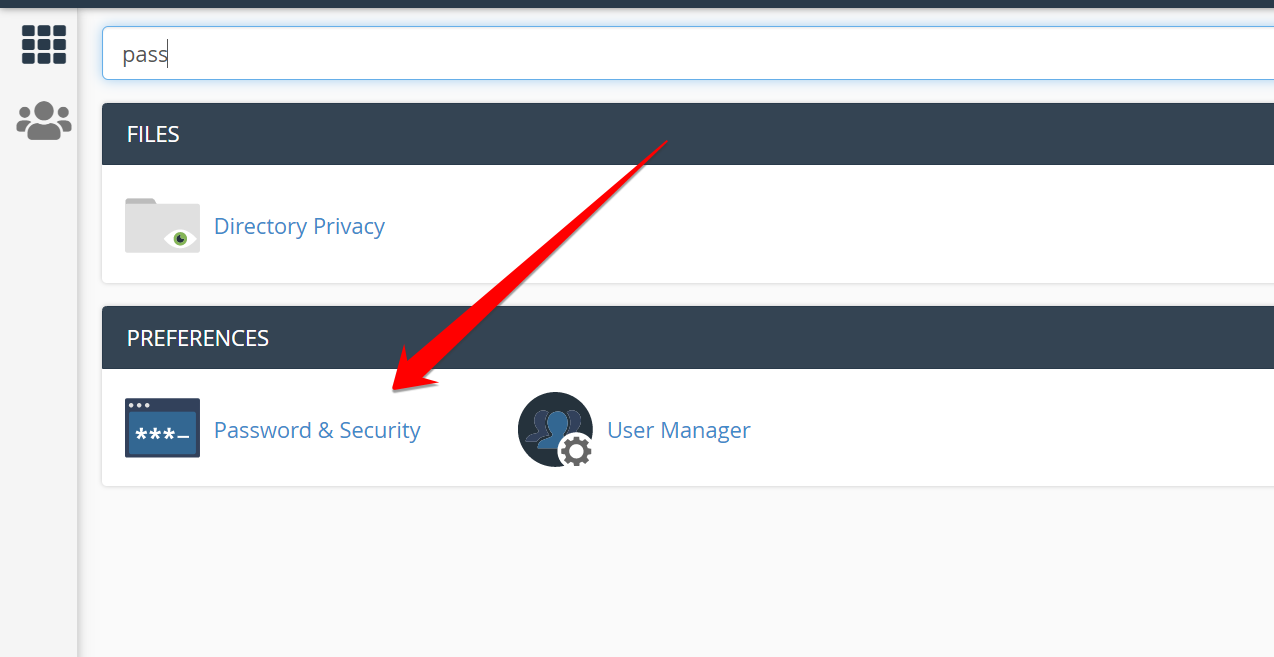
a) cPanel
Go to your cPanel and search for Password and Security to change the password.
b) Hosting Account
You should also change the password of your hosting company.

c) Domain registrar
It’s also crucial to change your registrar’s password since you might have used the same password for all accounts.

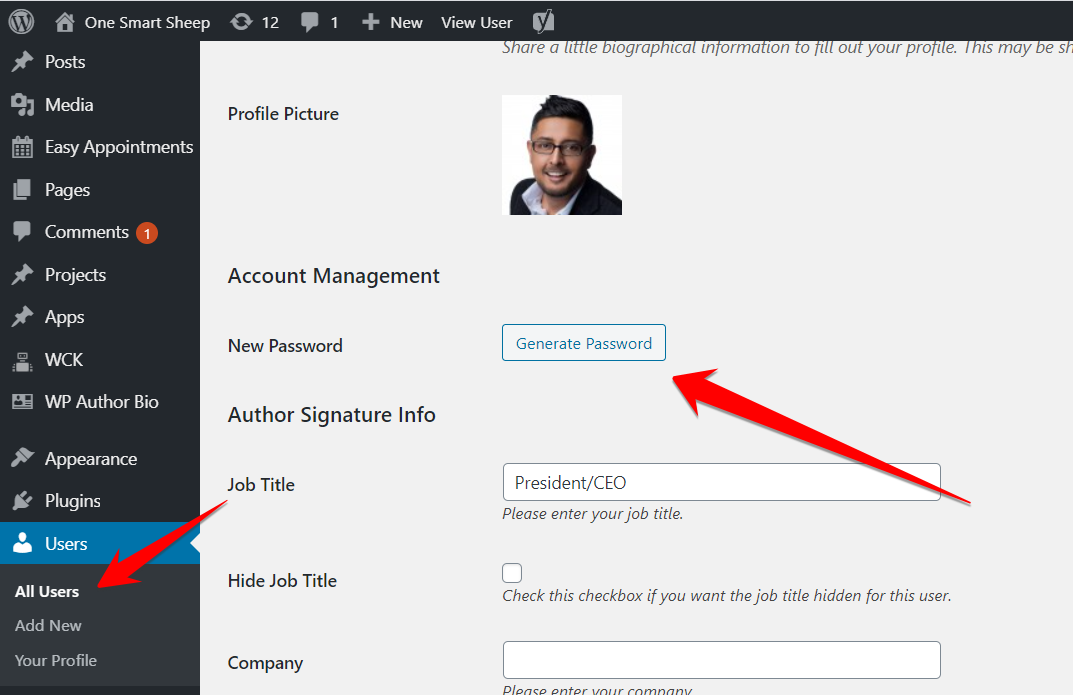
d) WordPress Users
Changing the password of all users is critical to secure your site. To change the password, go to All Users and click Edit. Scroll down to click the Generate Password button.
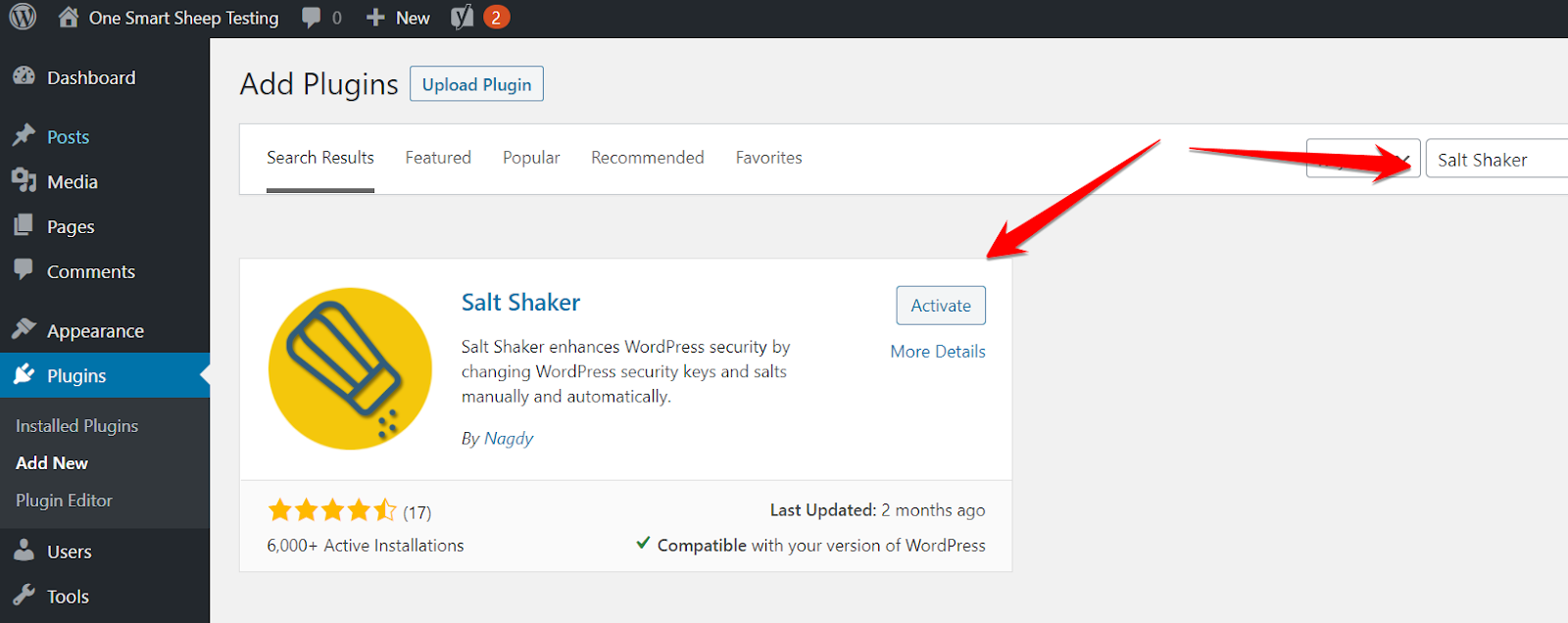
e) Changing Salt Keys
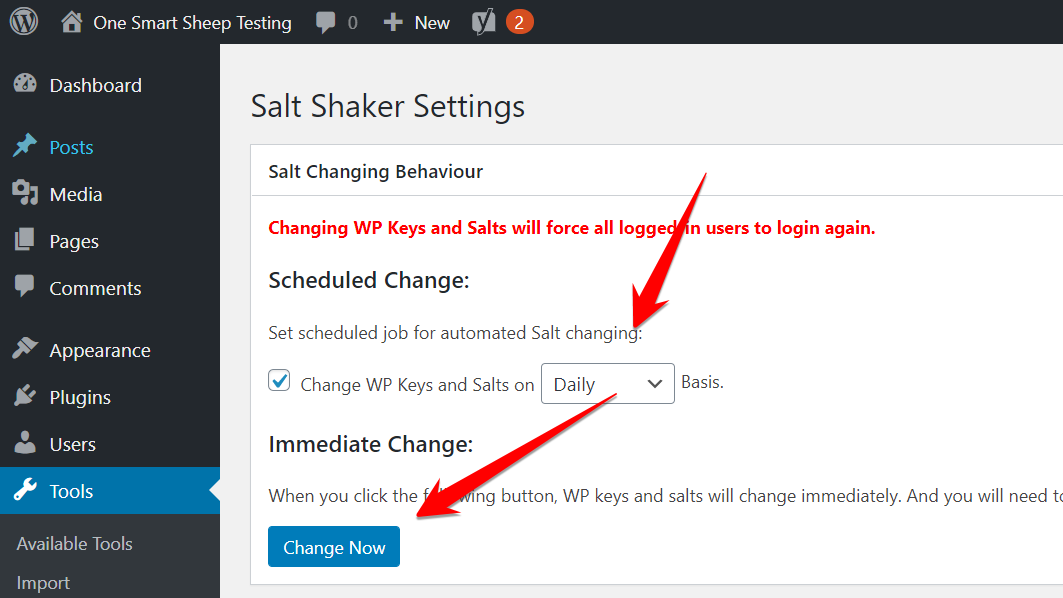
You should change Salt Keys if the hacker still has access to your site, which forces them to log out of your WordPress account immediately. The fastest way to change Salt Keys is with the plugin called Salt Shaker.
Go to Settings, chose Salt Keys daily, and hit Change Now.
Step 3: Scan Your Site
Scanning your website with different tools can help you to identify the potential malware living on your site. Malware and viruses are getting smarter each passing day thanks to machine learning, and tools are adopting the same technology to fight against them.I’ll show you different methods from basics to advanced.
a) Sucuri Scanner (Crawler)
Sucuri has a powerful tool that scans all the WordPress files and identifies the potential malware within a few seconds.It’s not always accurate, but can help you to figure most malware files.Go to Sucuri Scanner and type your website.
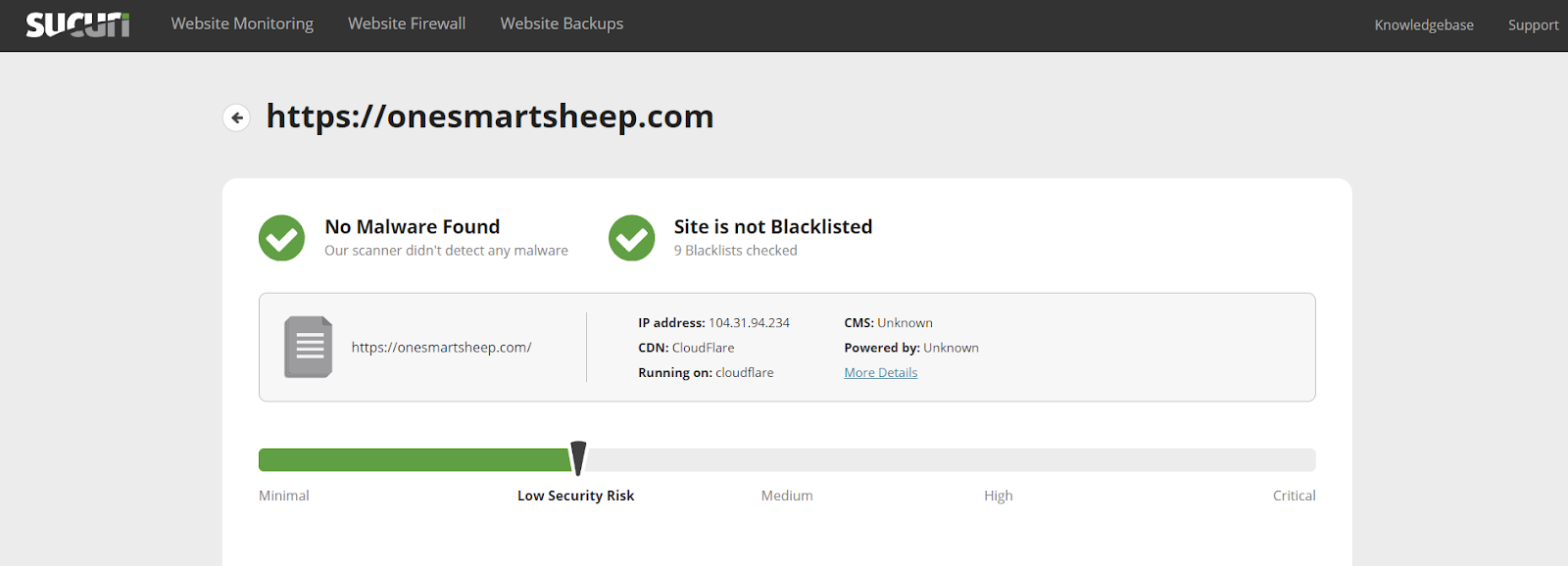
If any malware file is found, Sucuri shows the file’s location so that you can immediately delete it.
b) Isithacked Scanner (Crawler)
IsItHacked is another online tool that scans your website and reports malware if found.
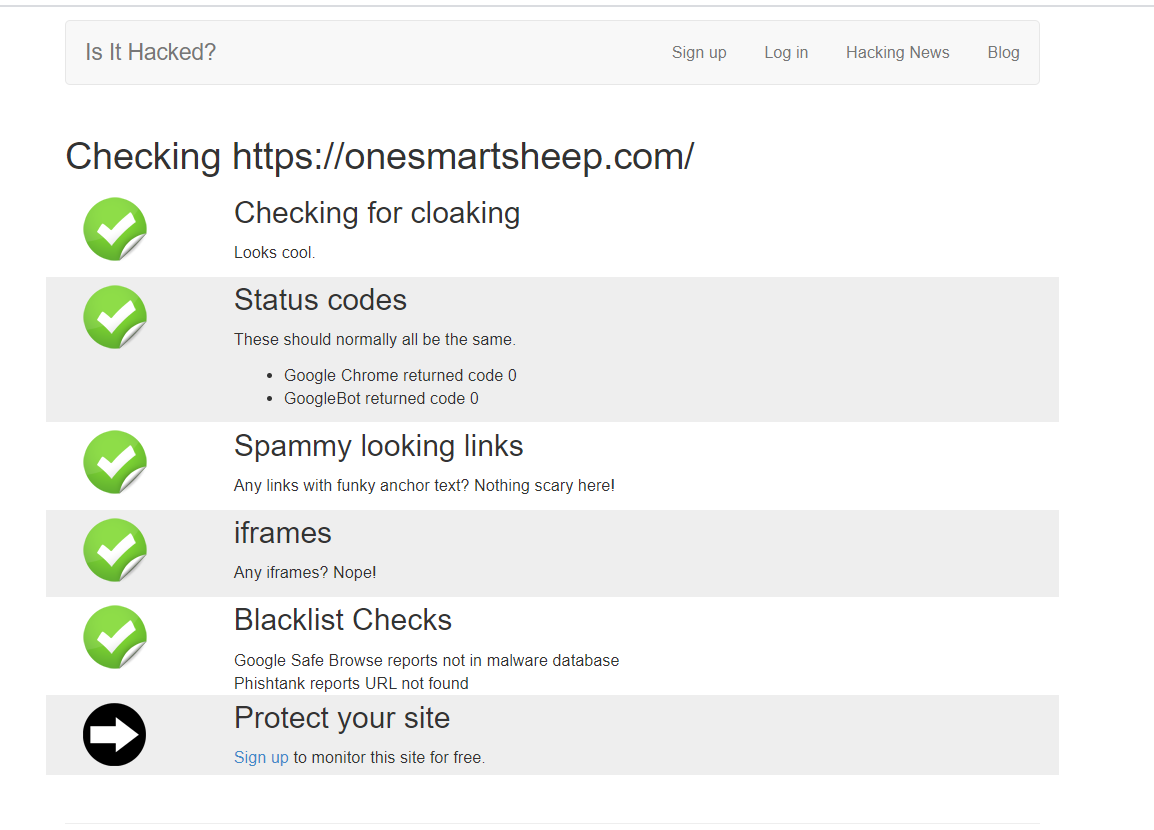
It also checks your website through different user-agents since hackers show the users’ real content but reveal different content to the search engines bot.
c) VirusTotal Scanner (Crawler)
VirusTotal is an extremely powerful scanner that uses 70 antivirus software applications to scan the files you upload.To take full advantage of VirusTotal, compress the essential files into a zip of your website and upload it to VirusTotal instead of just putting the URL that is not accurate. To make a zip, sign in to cPanel and click File Manager.

Go to the folder where your blog is installed. Select all the folder and files and click Compress.

Keep in mind that VirusTotal has an upload limit of 530MB. The Upload folder in the WordPress directory takes the majority of the space. You can ignore that folder.
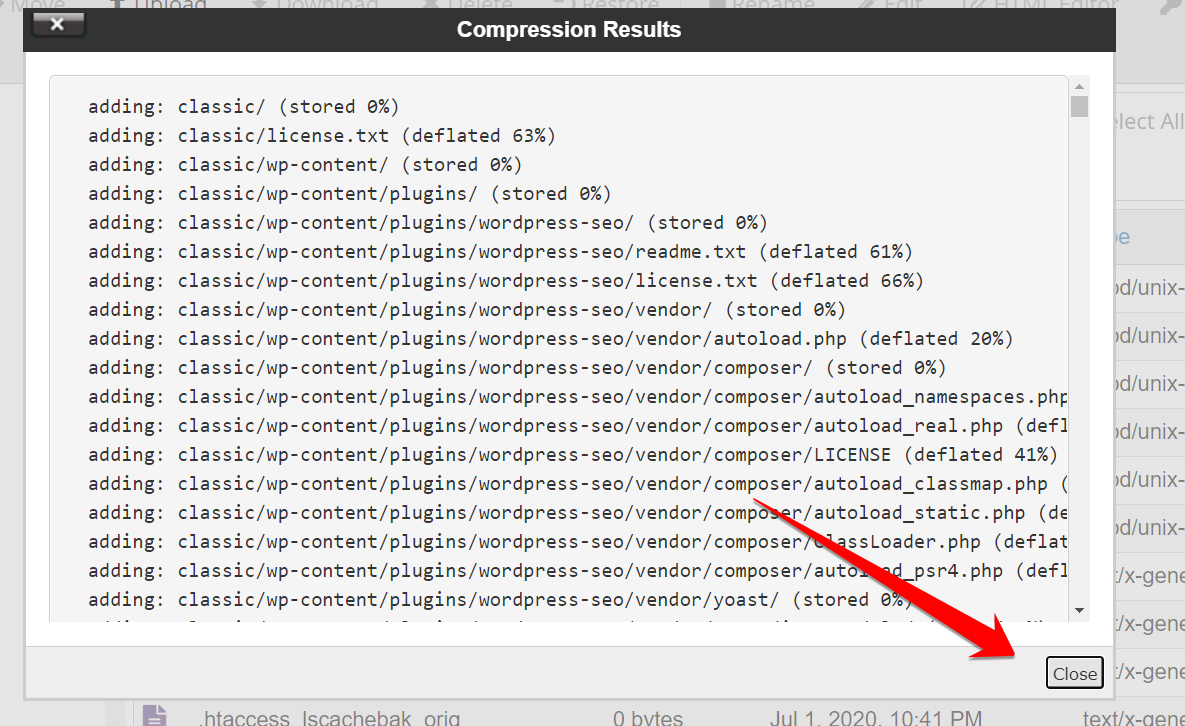
You’ll get this success message once your zip file is compressed. You need to download the file.

You can use any software to download the file.
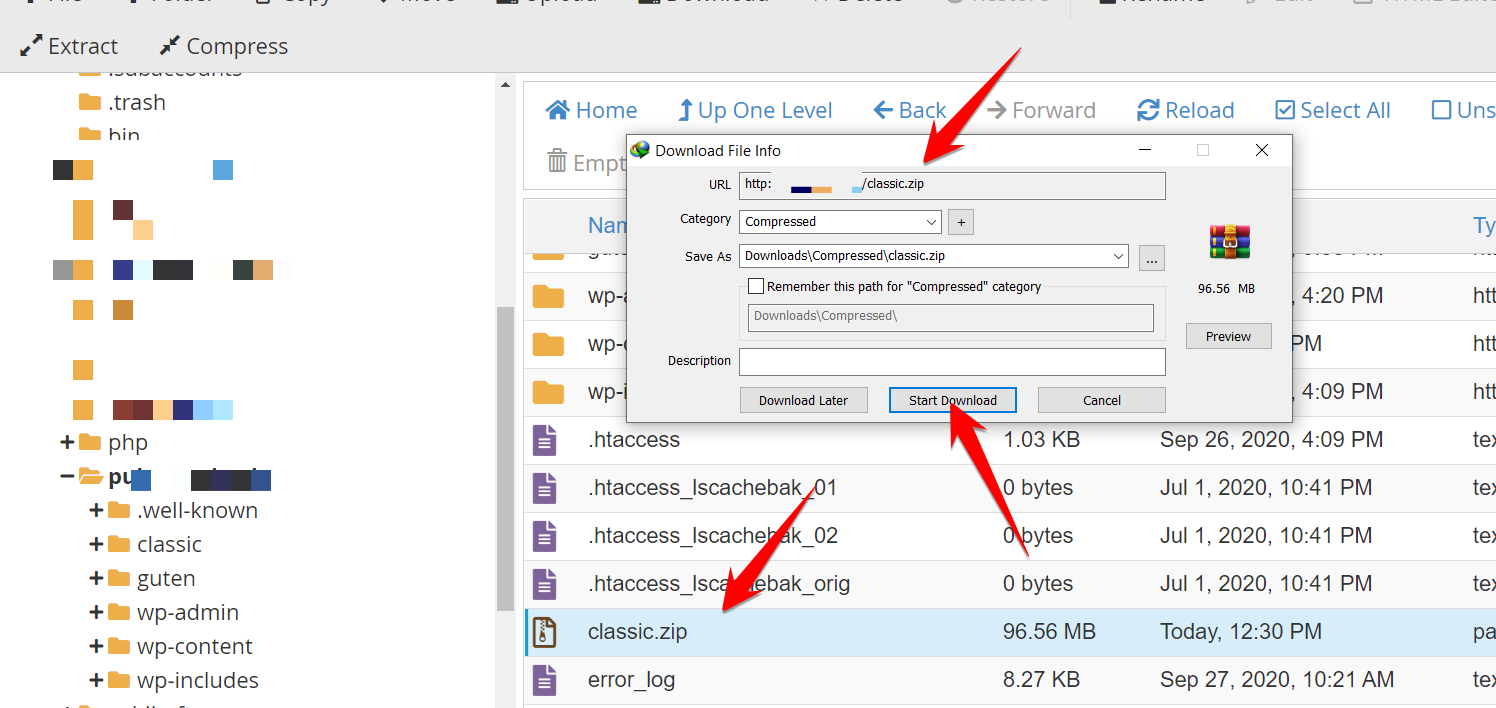
Because this file is uploaded in the root directory, the URL will become like this: https://yourwebsite.com/uploadedfile.zip
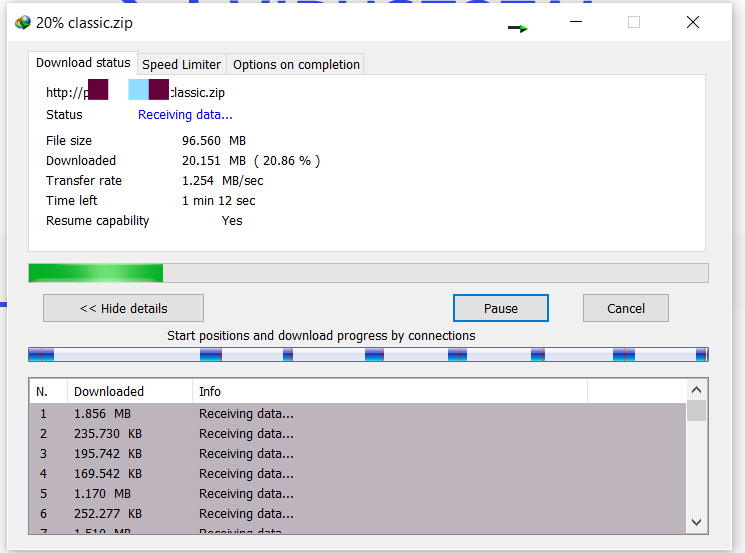
Once downloaded, upload to VirusTotal.
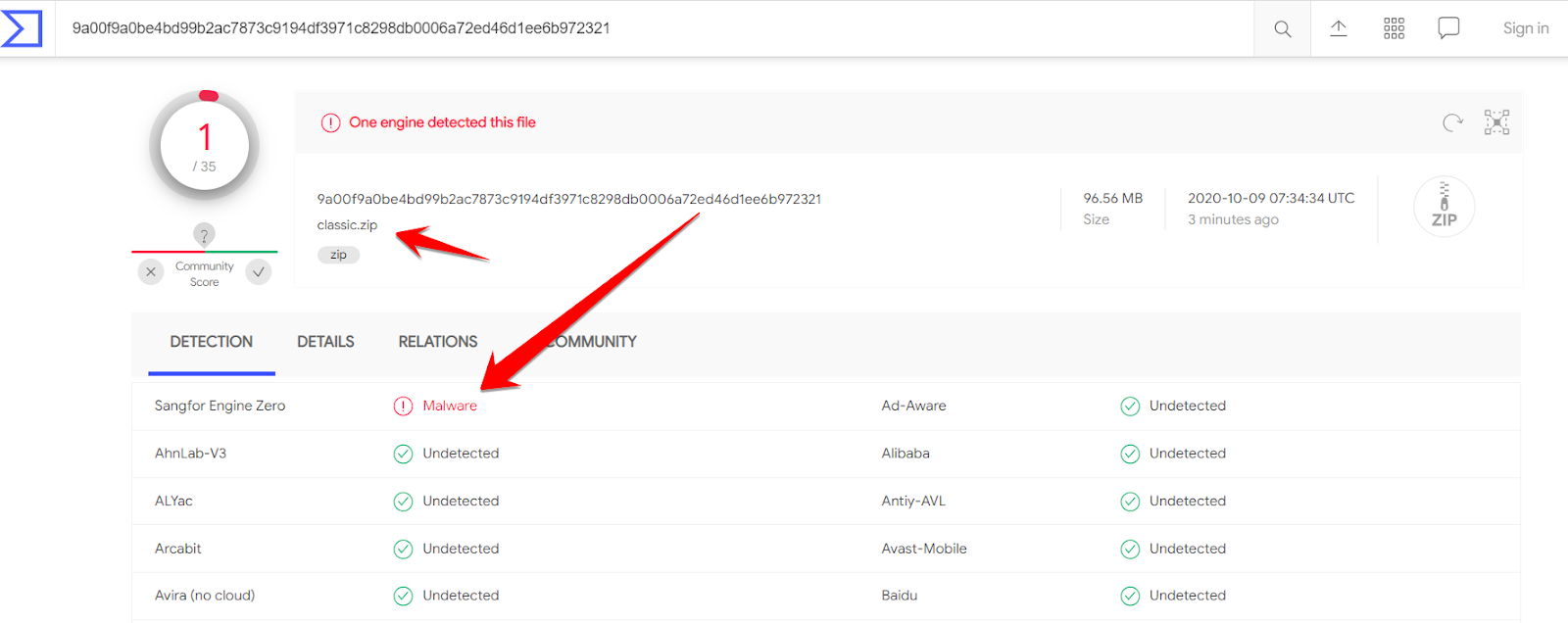
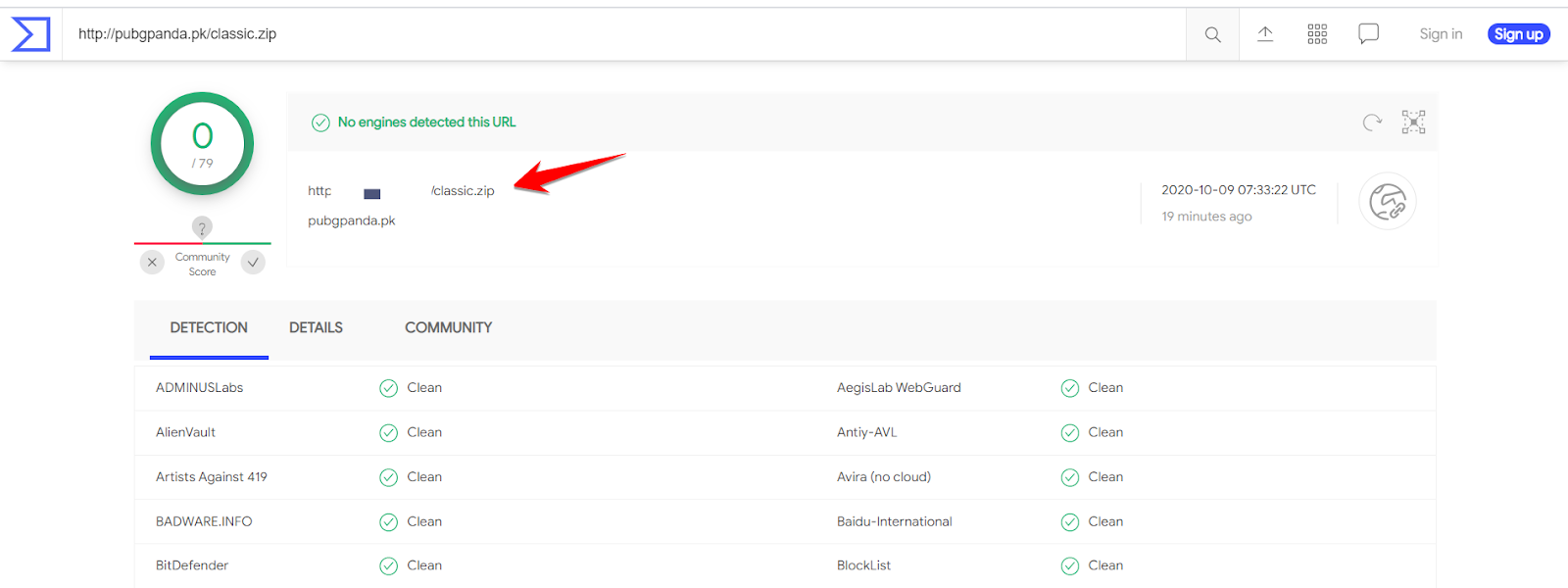
When you upload the file, you may get surprised like this. It shows the zip has malware and something is wrong with your website. You might be thinking, why I didn’t put the URL instead of the enormous size zip file? The reason is that VirusTotal is not powerful enough to download the zip file and scan it. Here is what happened when I put the URL into the VirusTotal field, no virus in the classic.zip.
d) Defender Malware Scanner (Plugin)
I found the Defender plugin to be the best malware scanner for plugins. I downloaded a virus file from the internet and uploaded it to the WordPress blog.
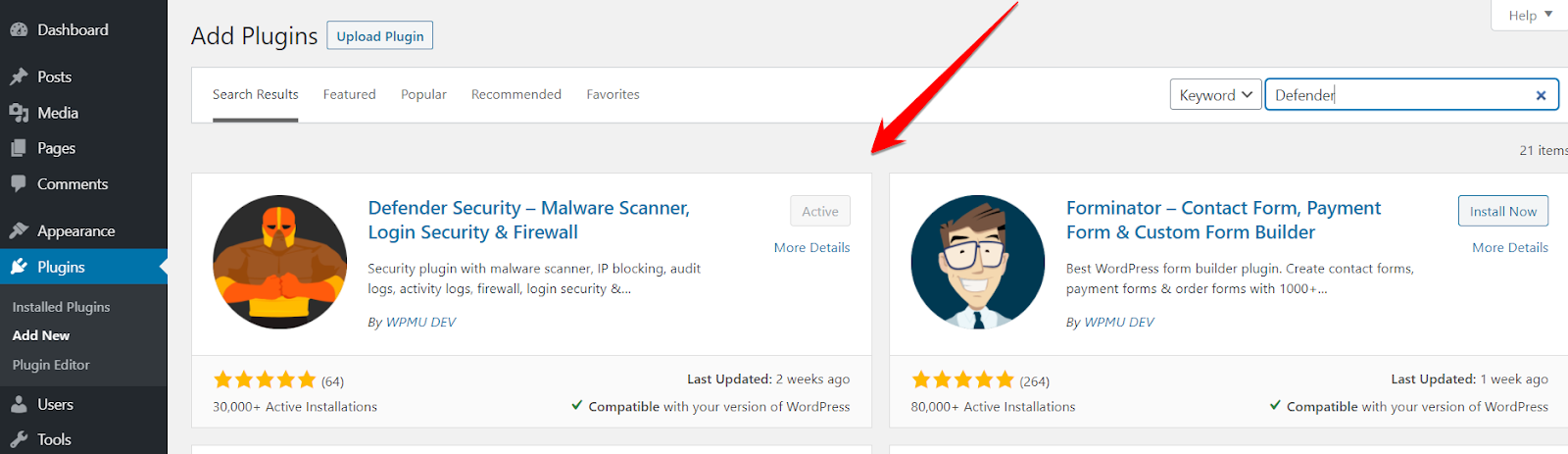
cPanel rejected the malware file, so I installed the File Manager plugin to upload the file.Did you know? Wordfence and other plugins didn’t detect the virus, but Defender did.

e) Wordfence Scanner (Plugin)
Wordfence is known as the best plugin when it comes to WordPress security. It has a built-in scanner that identifies malicious files and can delete them.Type Wordfence, install the first plugin that appears.

Go to Scan and start scanning your website.
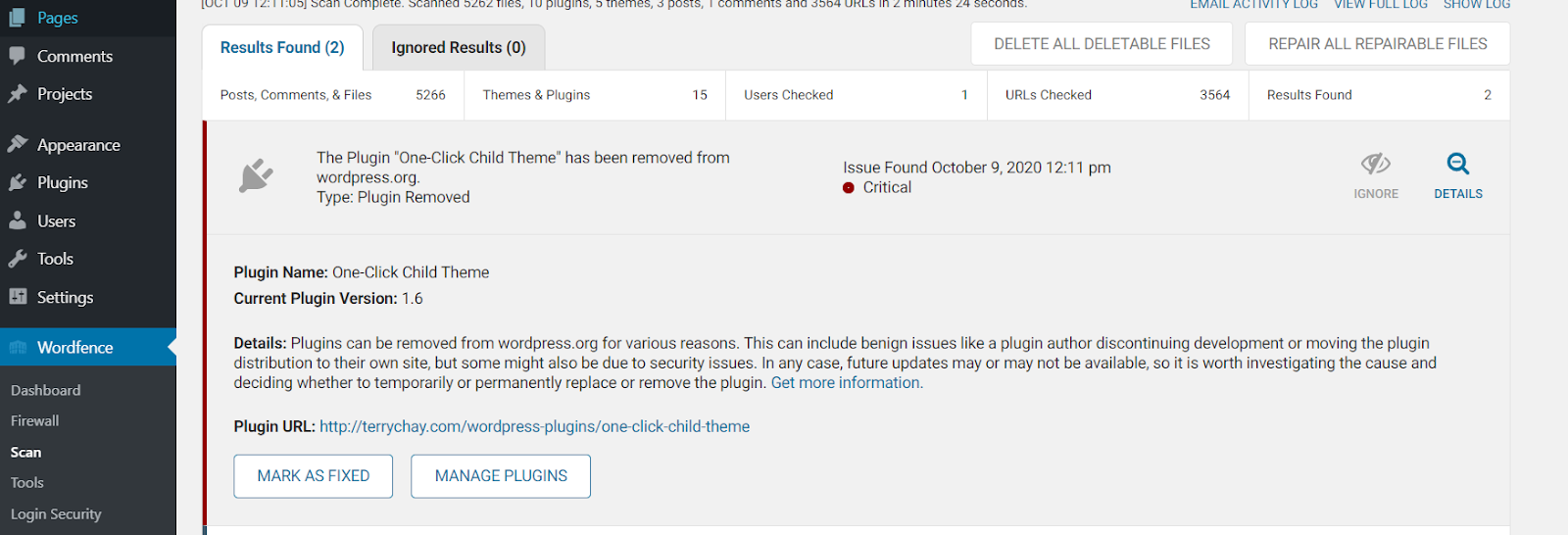
Depending on your website’s size, it may take some time and provide additional information about the critical issues.If you find a malware file through Wordfence, you must immediately delete the file.
f) Malcare Scanner (Plugin)
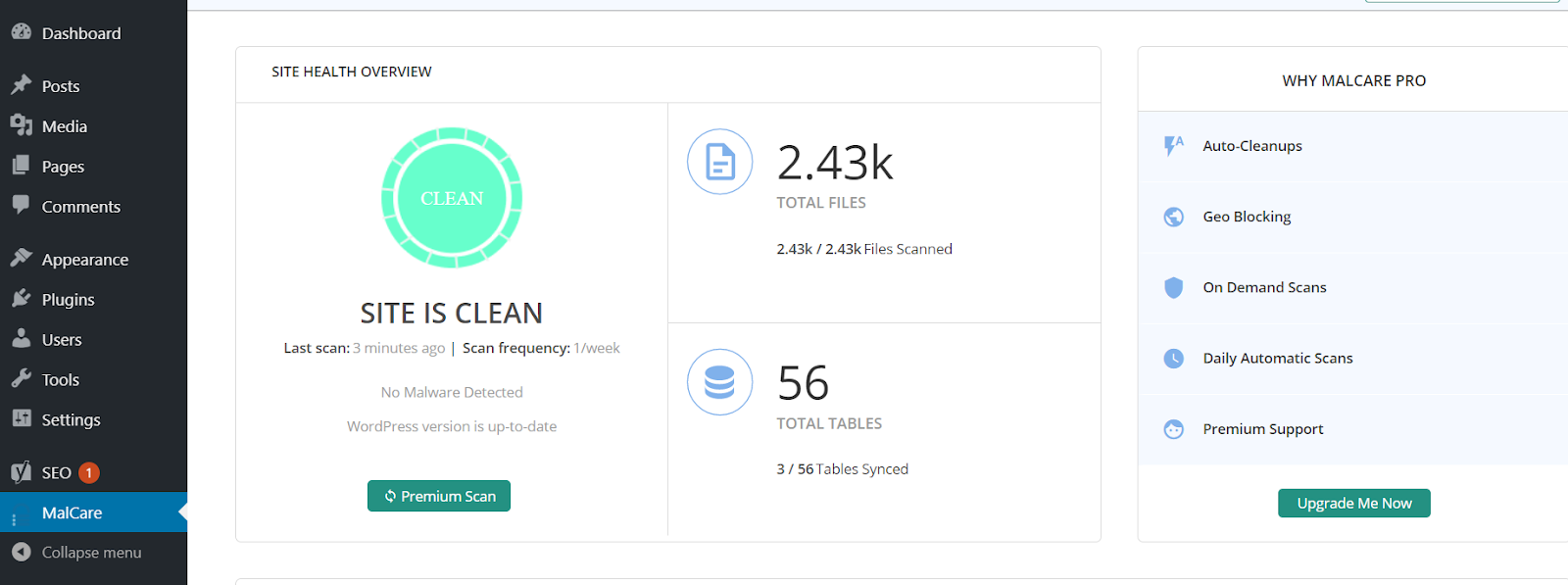
Malware Scanner is another excellent addition to the malware scanner for WordPress.It doesn’t slow down your WordPress since it runs on the cloud: faster and better.Install the plugin from Plugins and activate it; it starts scanning once you hit scan now.

Once your site is scanned, it provides you with the report.
Step 3: Check Recently Modified Files
So, you have scanned your WordPress website, now what? You need to delete the files found suspicious and check the CPU usage by restarting your hosting server.If the CPU usage is still high, it means the malware is still active on your blog.I’ll show you two ways:
a) cPanel
To check the recently modified files, go to the folder where your WordPress is installed.
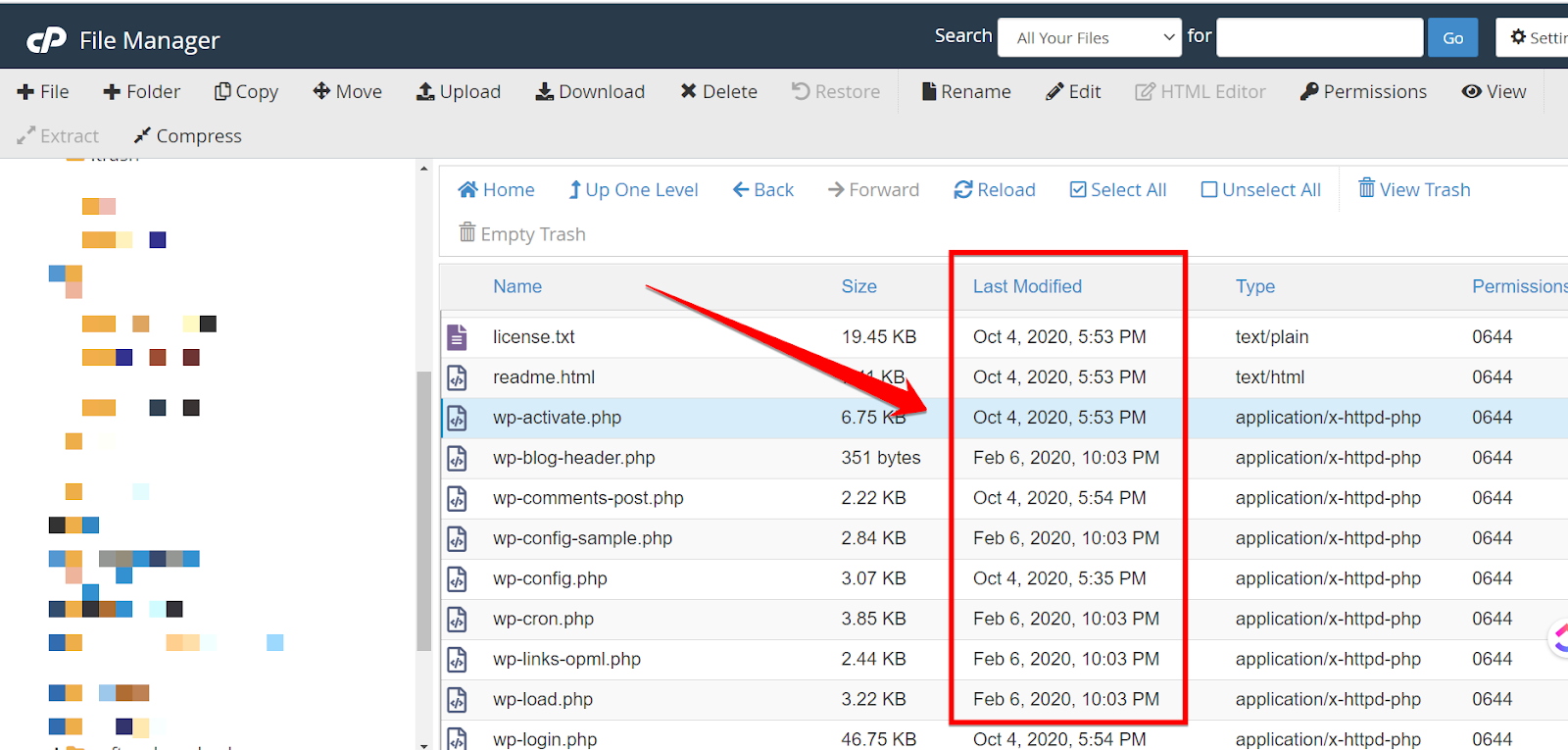
The files modified in the last 7 days should be taken into account.Download the original WordPress zip from the official website.

And extract it.
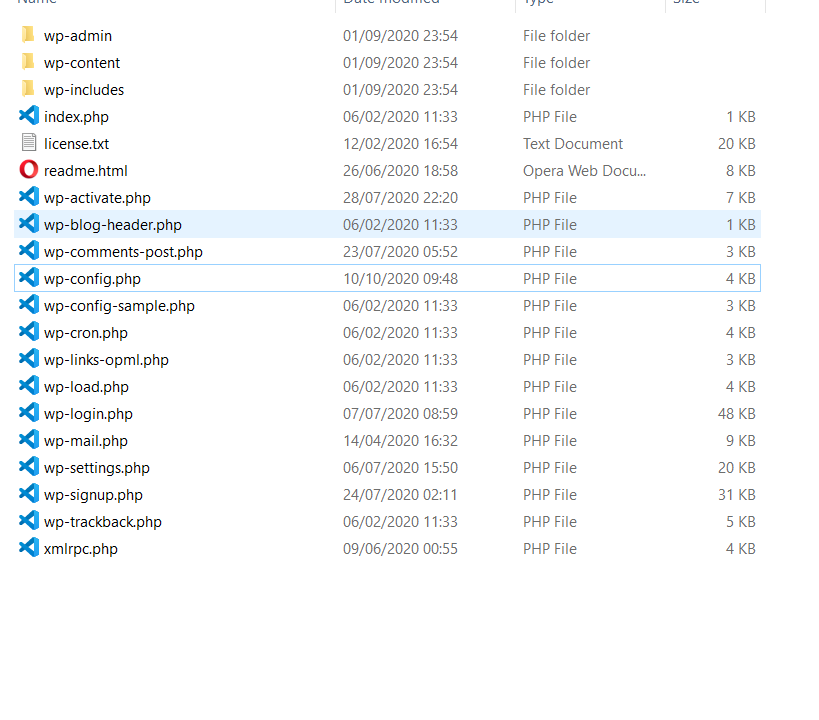
Install and run Microsoft Visual Studio Code. Go to File and open the folder that we extracted.

Once you open the WordPress extracted folder, it lists all the files and folders.
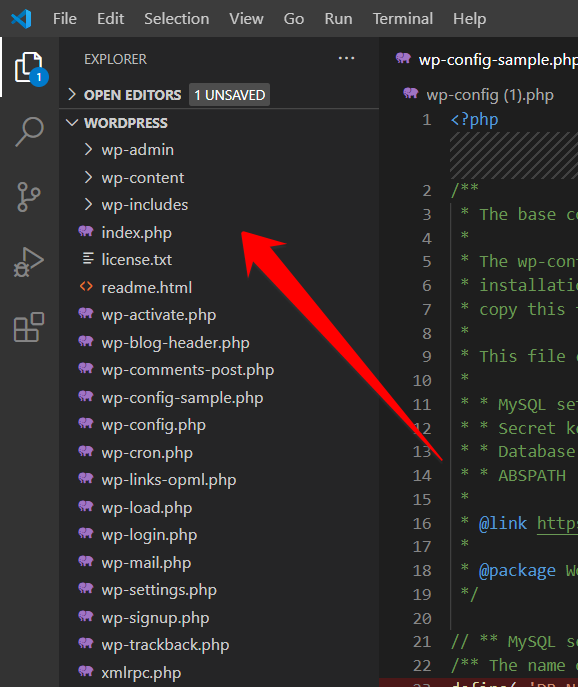
Paste the modified file that you downloaded from cPanel into the WordPress folder; I picked wp-config in my case.
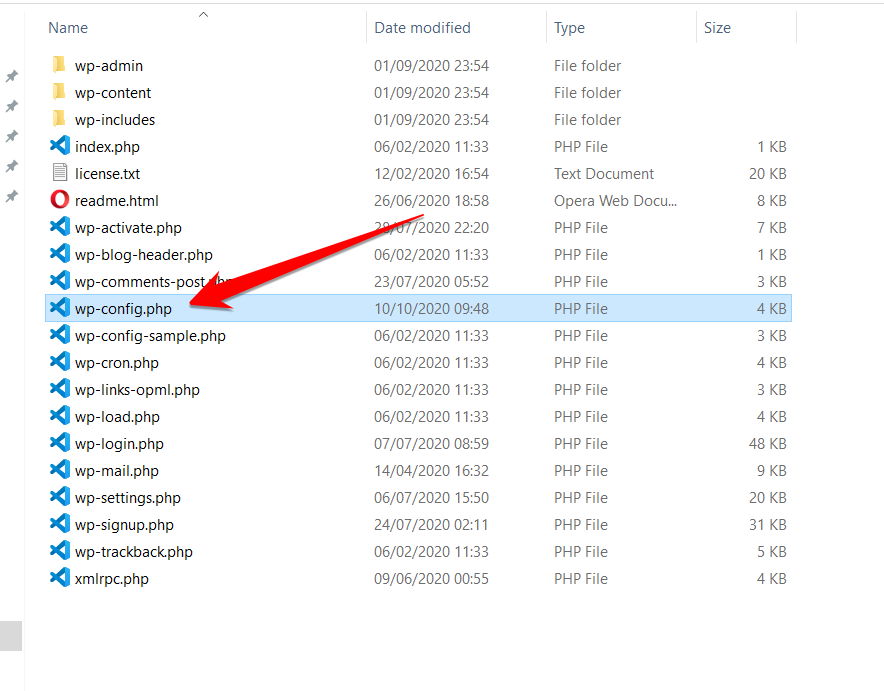
Select two files of the same nature using the Ctrl button (Control in Mac) and click COMPARE SELECTED.
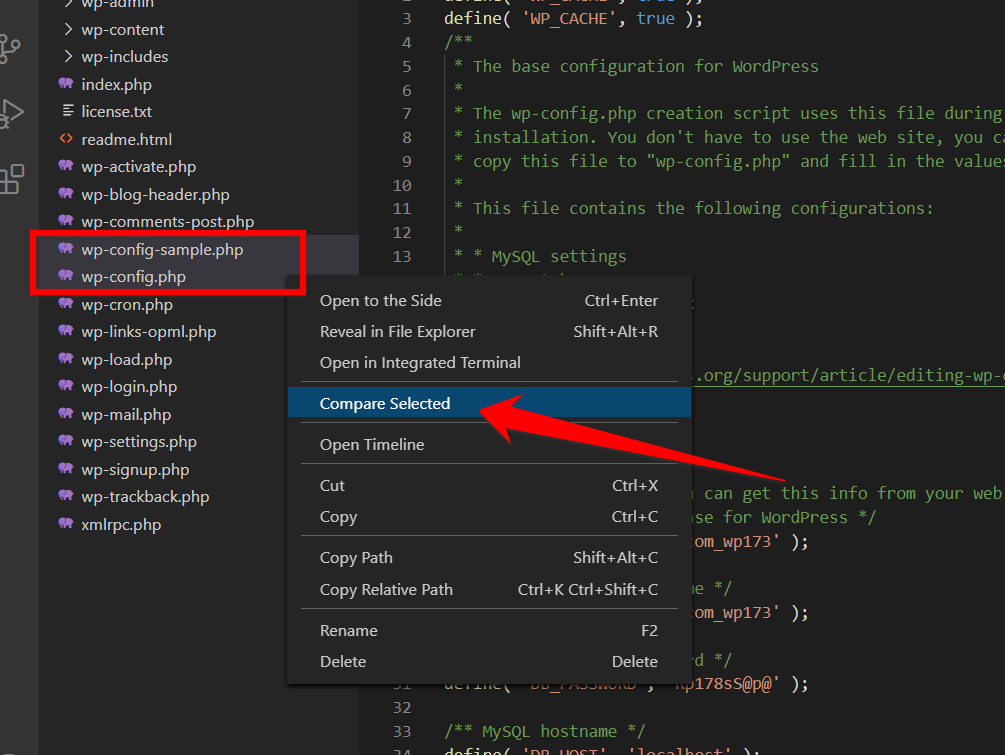
VS Code will show you all the changes that have been made in the files.
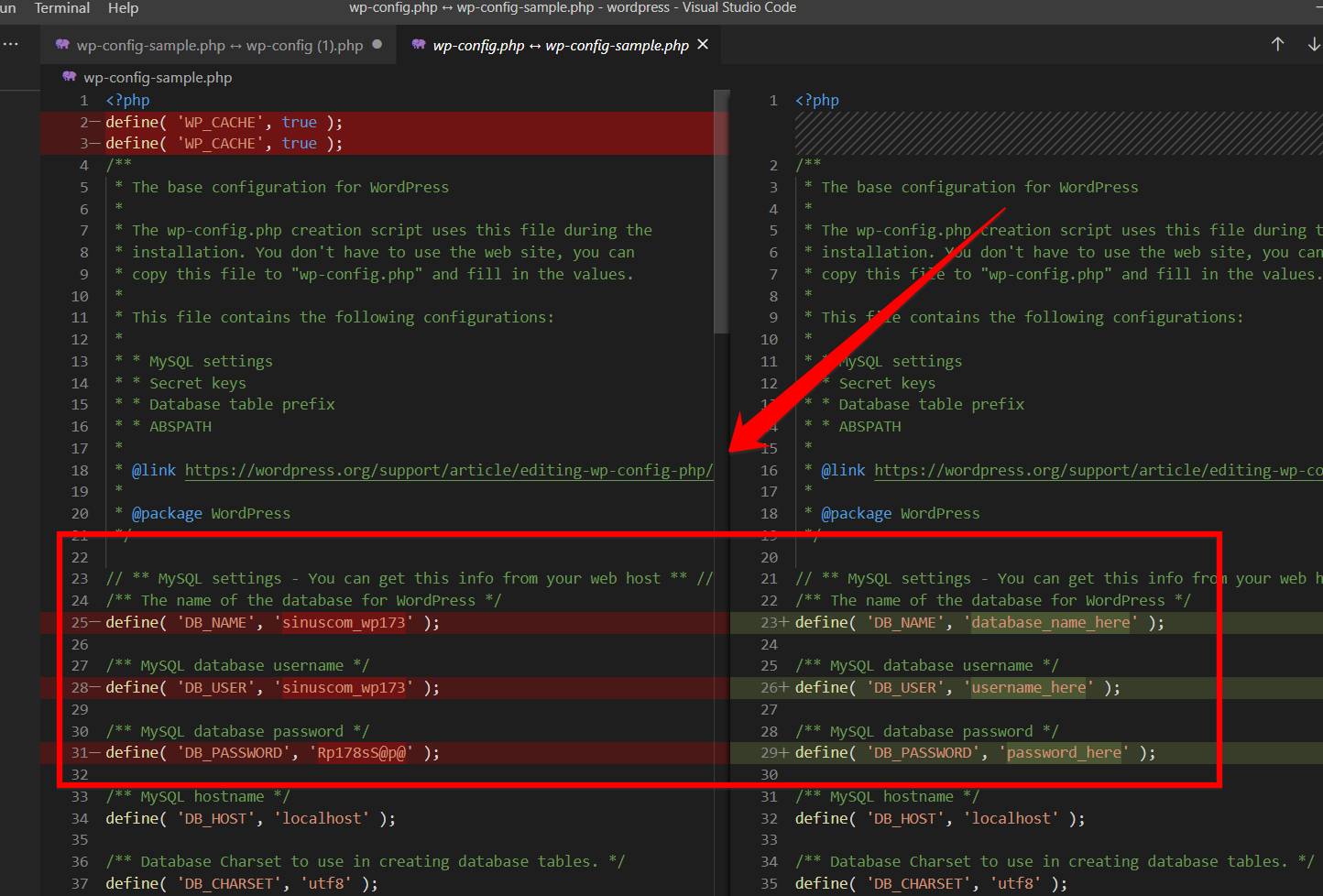
If you have a little programming language experience, you can quickly identify the malware pattern. Keep the SSH section to learn more about the pattern.
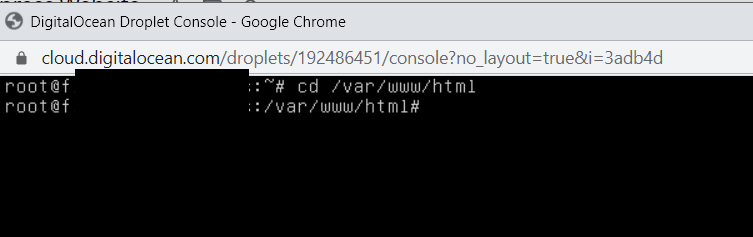
b) SSH
If you’re using DigitalOcean or any cloud hosting service, you can easily find all the files with a command that has been modified recently. Open your SSH (also known as Console access) and open the below command to enter the directory where your WordPress is installed.cd /var/www/html
And now enter the below command:find . -type f -name '*.php' -ctime -7
It will provide you with all the PHP files that were modified in the last 7 days.
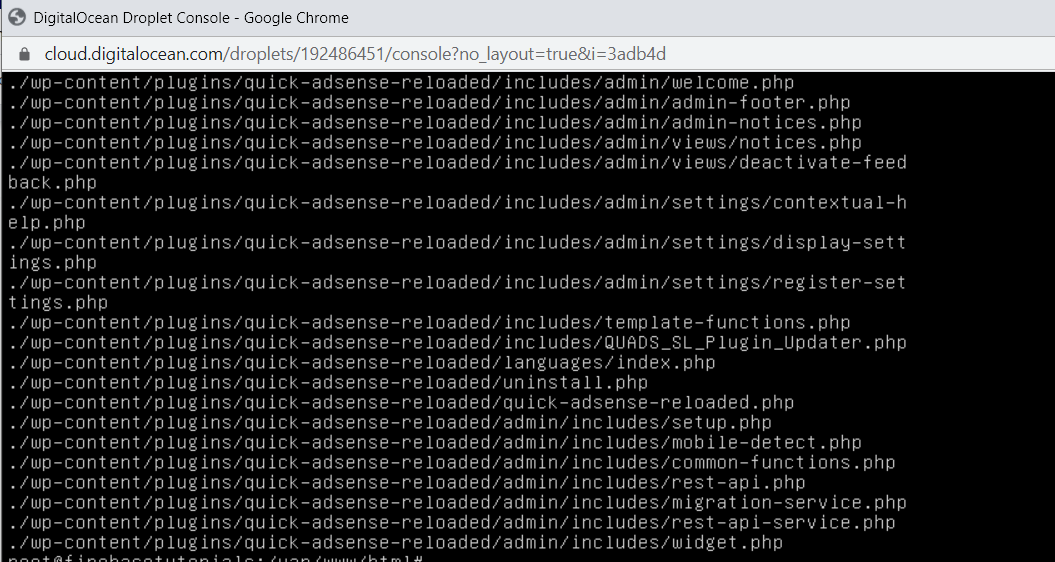
If you want to see the JS files that have been modified, try the below command:find. -type f -name '*.js' -ctime -7.js indicates the javascript and -ctime -7 shows the; modified files in the last 7 days. You can enter any number, for example -ctime -1. And if you want to list all the files modified in the last 10 days, you need to type the below command:find ./ -type f -mtime -15
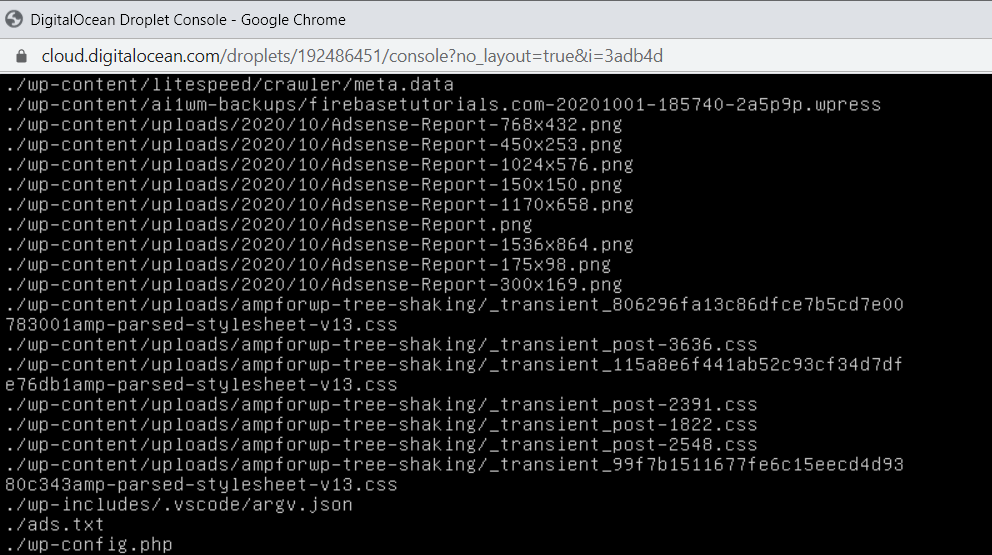
Some functions that are very commonly used in backdoors and obfuscated malware are
- eval()
- base64_decode()
- gzinflate()
- str_rot13()
- base64 str_rot13
- gzuncompress
- eval
- exec
- system
- assert
- stripslashes
- preg_replace (with /e/)
- move_uploaded_file
Note: Some plugins might use the above functions, test your site after you remove the functions; otherwise, you may break your website.
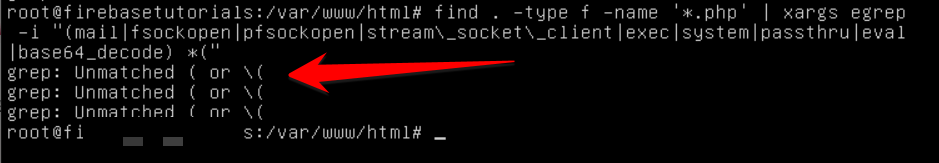
On my website, there is no such file; I got an unmatched error.
Step 4: Delete the Malware Files
Clean the following malware files:
- Suspicious files are shown by malware scanners like Defender, Wordfence, and Sucuri.
- Removing malware files that you found by harmful patterns and functions explained in Step 3.
Once you’ve deleted, restart the server if you’re using cloud hosting or talk to your hosting provider.When you see low CPU usage, and everything is working as expected, go to Google Console and click REQUEST REVIEW.

Note: Make sure you’ve deleted all the URLs and folder mentioned in the Sample URLs.Once you’ve requested the Review button, and you don’t get any warning in return, it means you’ve successfully made your WordPress website clean from all types of malware and viruses.
Step 5: Create Backups
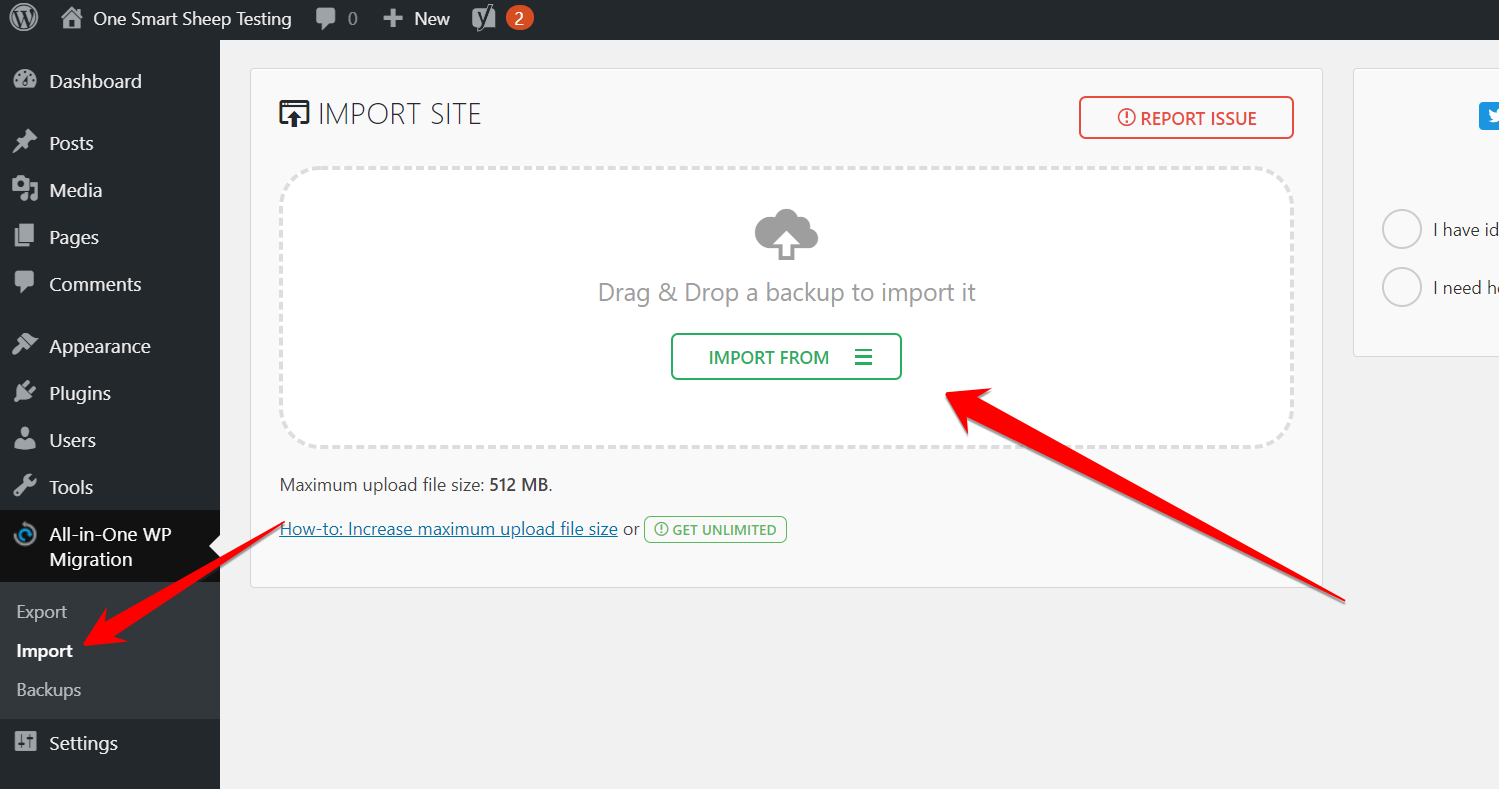
Create a backup of your complete WordPress blog before you celebrate the win against the hackers.How do you make a backup? Install All in One Migration plugin and activate it.
Go to All in One Migration, and click Backup.
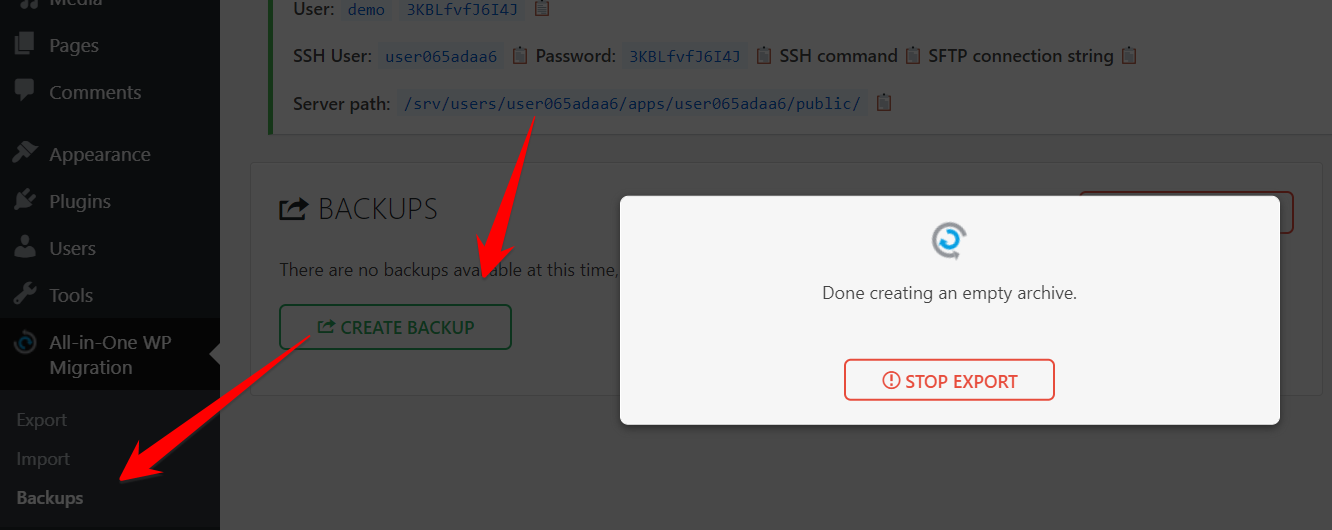
Depending on your WordPress site’s size, it may take a few minutes to create a backup. Once completed, you’ll get this message. You can download it and store it on your laptop.

If you want to import in the future, just go to Import and upload the file.
Why WordPress Gets Hacked?
It’s common among hackers to target the software with the vast majority of market share. Of course, it makes more financial sense for hackers to target Windows than Linux. The same is the case with WordPress having a market share of more than 38%. Being open-source in nature, it opens doors for hackers.Here are the top reasons WordPress gets hacked:
1. Insecure Web Hosting
Many people always opt for cheap hosting that becomes the number one cause for being hacked. Most cheap hosting companies don't help people. They don’t care if your website gets hacked or goes down for hours. You get what you pay for. Whatever web host you use, check the reviews on the internet.Look for the bad reviews regarding hacked WordPress sites. I recommended you must check the overall rating of the hosting company before you purchase any plan.
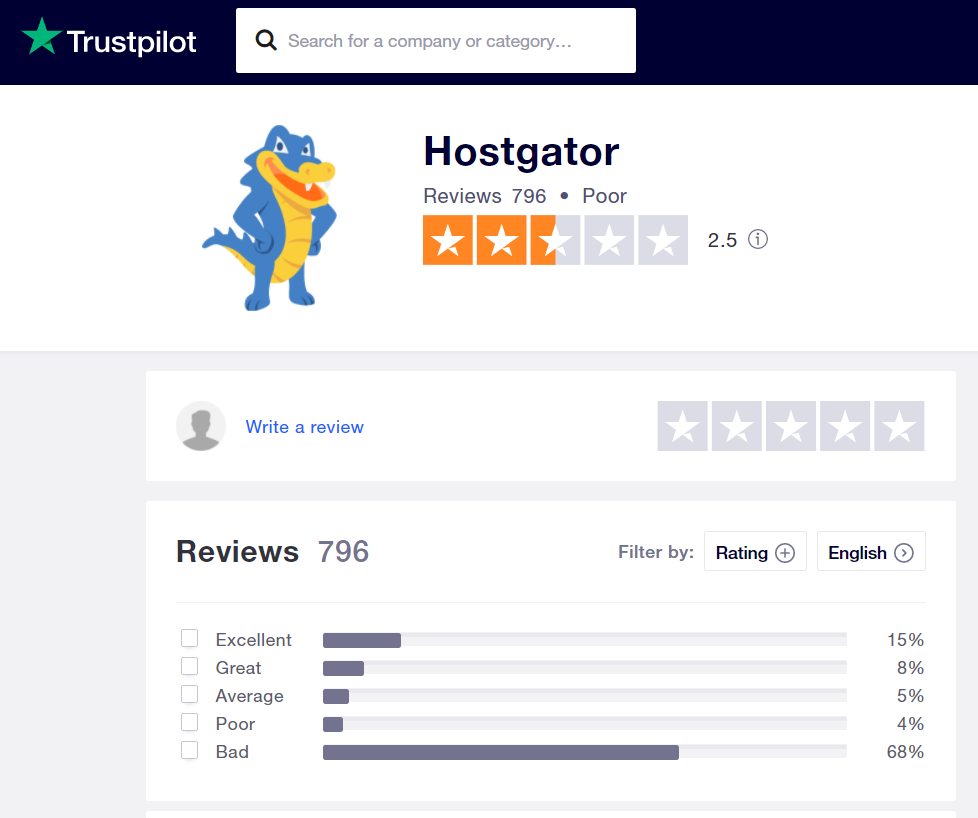
Then find out the reviews to see how the company dealt with the hacked site.

It clearly indicates that Hostgator isn’t a good company. Many hosting companies have a long track of being hacked due to using outdated security standards.
At One Smart Sheep, we host our clients’ websites on ultra-high-speed servers and offer services for maintenance, fixes, repairs, and much more at an affordable price.
2. Using Weak Passwords
If your WordPress website has a weak password, hackers don’t need to even attack your network to compromise it.Before you set a password for:
- Users
- FTP
- WordPress login
Use haveibeenpwned.com that scans your password among thousands of data breaches.
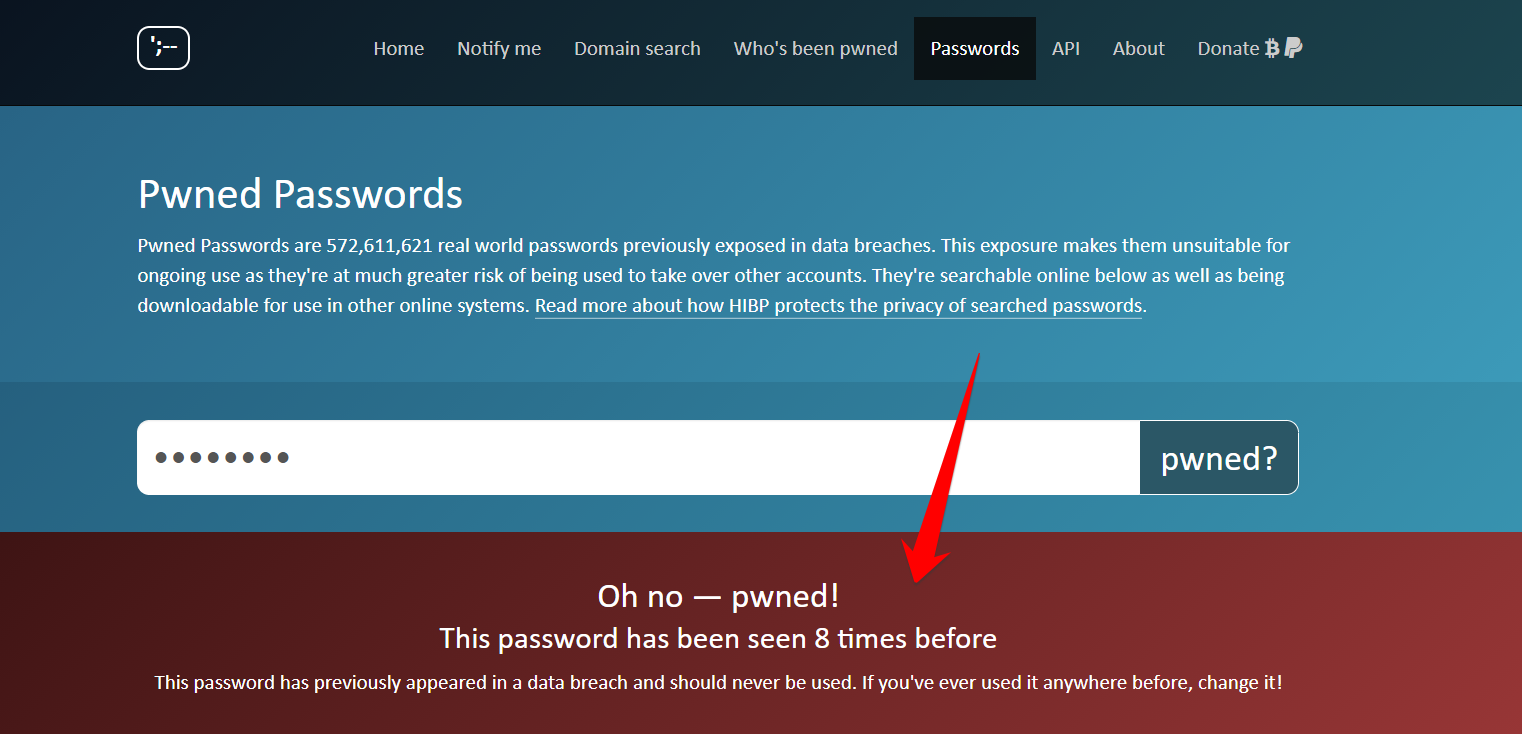
Hackers download leaked password databases consisting of thousands of gigabytes of data and attack a WordPress website with brute-force. A brute-force attack consists of an attacker submitting many passwords in the expectation of ultimately guessing correctly. The best practice is to change your password frequently once a month of your important accounts. Don’t forget to use Google Alert if your hosting gets hacked; you can immediately secure your website.
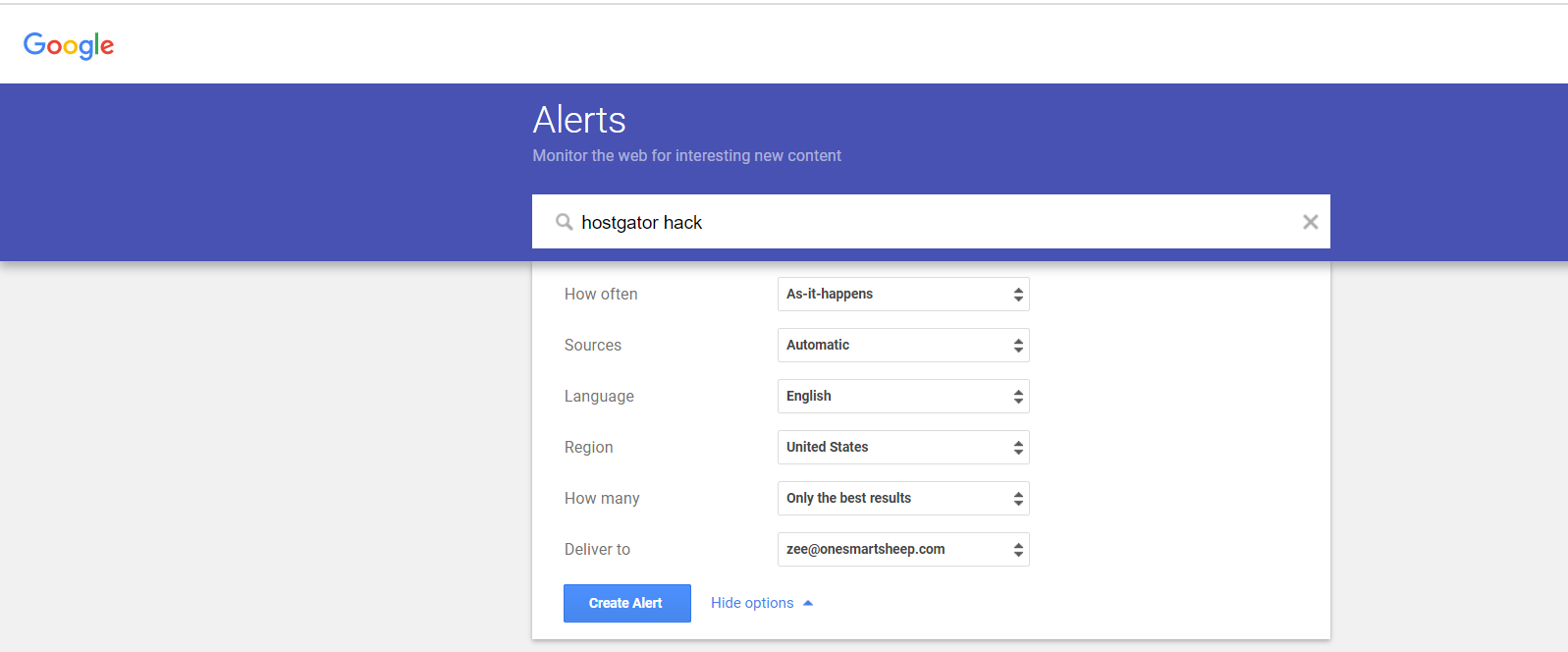
3. Not Updating WordPress, Plugins, or Themes
Most WordPress updates are related to security patches that fix a potential vulnerability. Did you know that WordPress has introduced auto-updates features in the latest version? It means users can set their plugins and themes to update automatically, and security patches are applied without the user’s consent.After installing the latest version of WordPress, go to Installed Plugins, and enable auto-updates.

To enable auto-updates for themes, go to Appearance>Themes. Select the WordPress theme, and hit Enable Auto-Updates.
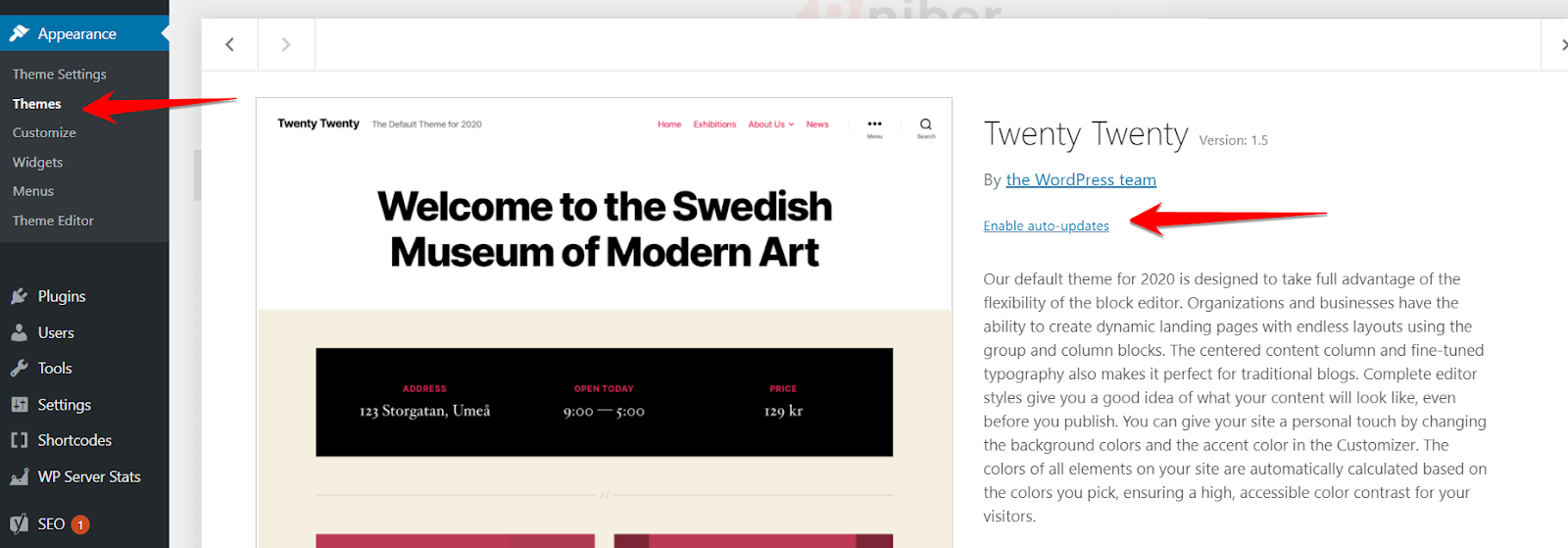
Keep in mind that the themes you purchase from the marketplace, like ThemeForest, may not offer auto-update features.
4. Nulled Themes and Plugins
People love free stuff, so is the case with nulled themes and plugins that can be downloaded for free on the internet.

The primary issue with nulled stuff is that they contain dangerous viruses and malware.Hackers install dangerous scripts in plugins and themes that later help them access the entire website without any registration, and you may have no idea what’s going on behind the scenes.The key takeaway? If you’ve installed any nulled thing, you should immediately delete it from your WordPress.
5. Playing Wrong with FTP
Most users play with different settings with FileZilla and cPanel that end up making their websites being hacked.How does it happen? Suppose a user had an image upload issue, and he made the wp-admin folder publicly available by watching a tutorial on Youtube.

But he is happy as he has fixed the issue, but actually, he made a blunder. Hackers can take complete control of the website.Don't make such a mistake.
How to Check If Your Website Is Really Hacked?
It’s critical to check either your website is really hacked or your mind is just making you scared.Here are the top 4 ways:
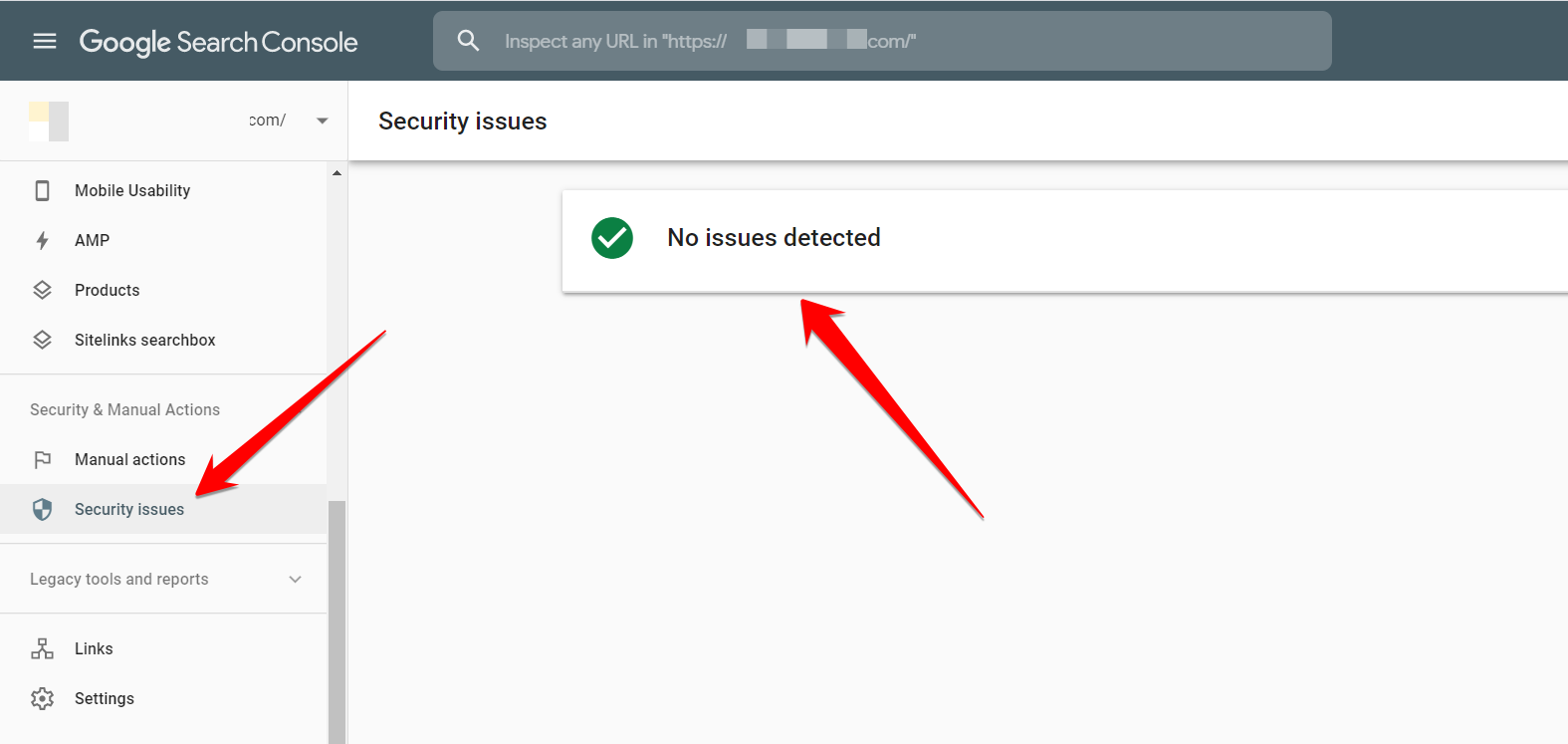
1. View “Security Issues” in Google Search Console
Google doesn’t only help you rank higher on Google, but also detect malicious files on your blog. Even if you had not installed Google Console when your site was hacked, Google Console could show the malware files instantly after installing it.
2. High CPU Usage
Modern malware programs are smart. They may not harm your site directly but may use CPU to make money, primarily through cryptocurrencies.Furthermore, high CPU consumption indicates the malware program is active on your website and performing different suspicious tasks ranging from encrypting your essential files and downloading secrets data.You can use several ways to identify if your WordPress is consuming a high CPU. Log in to your cPanel, and locate Resource Usage that falls under Metrics.
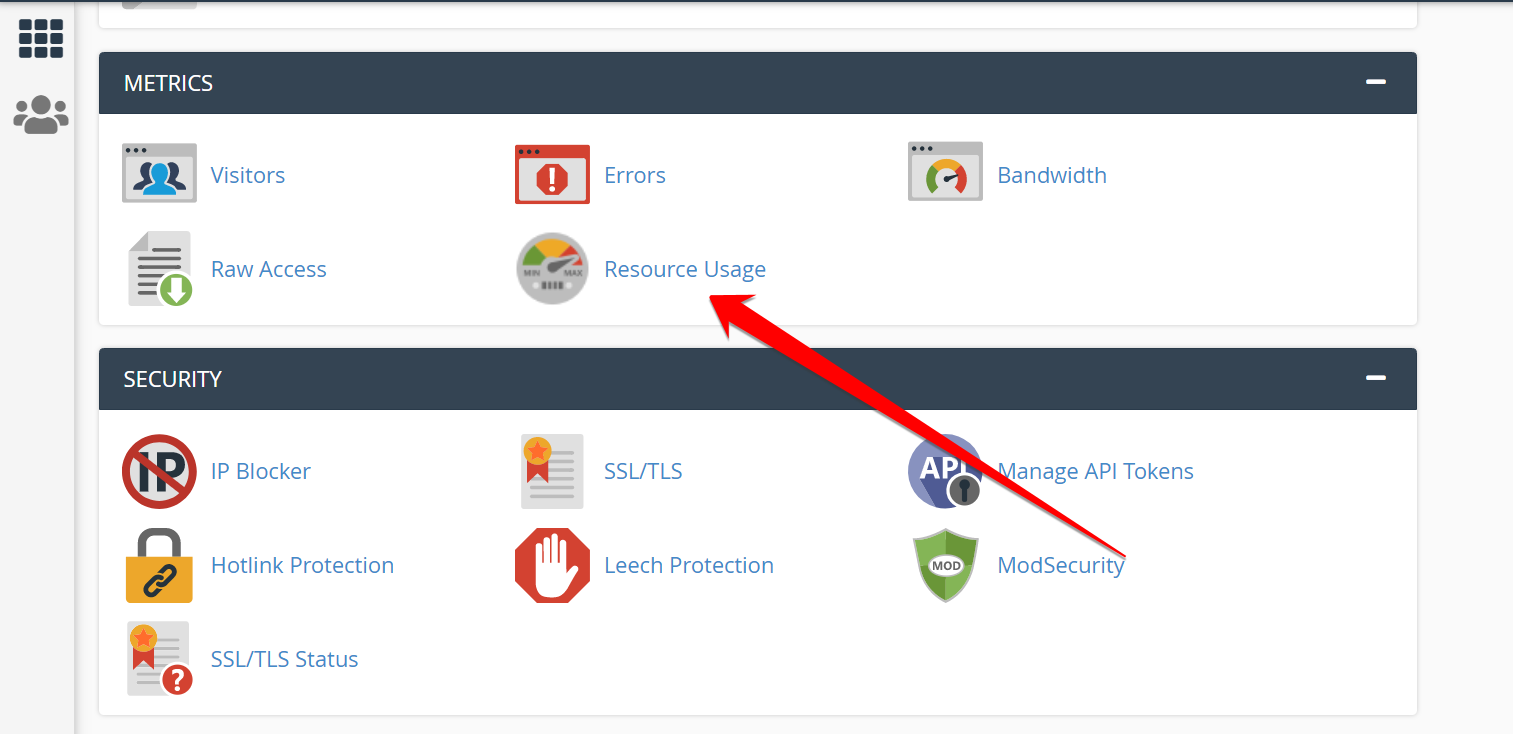
Scroll down a little, and you’ll see the simple graph. The green line indicates the average usage of your CPU.
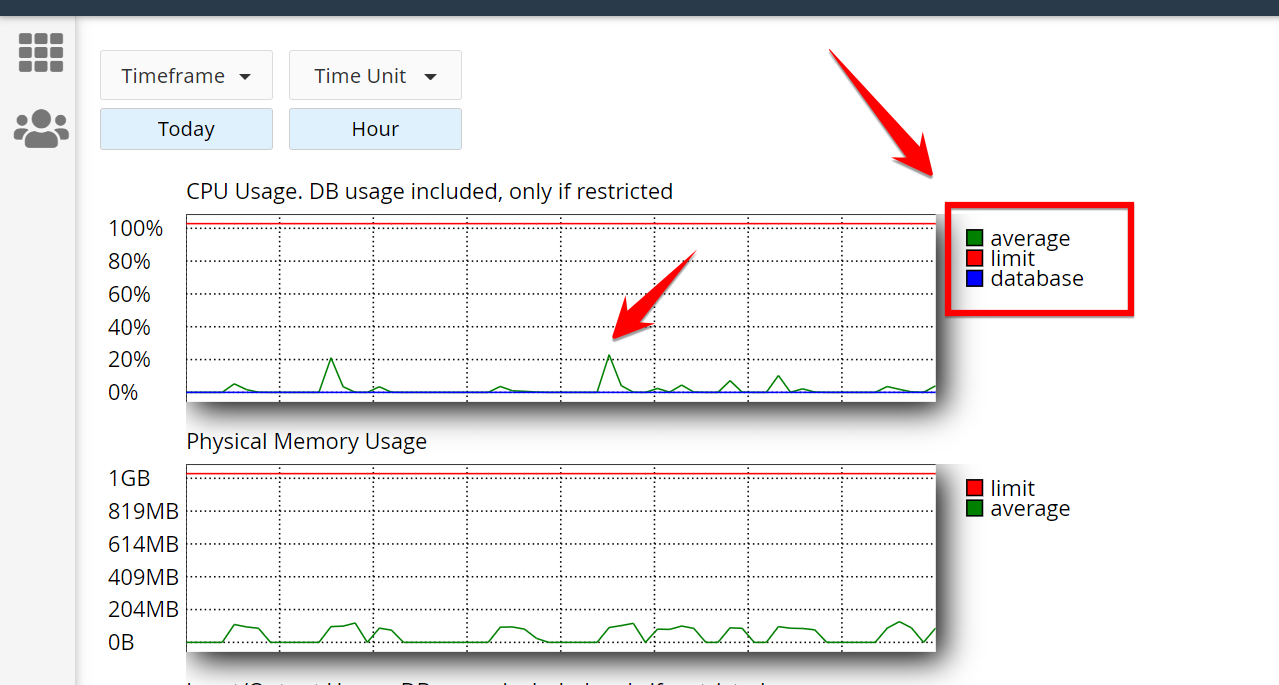
If you see the average usage percentage above 70% to 90%, it means your website in hot water and should be investigated which processes are taking most of the CPU. If you’re using a cloud hosting like DigitalOcean, you can quickly check CPU usage in the Metrics section.
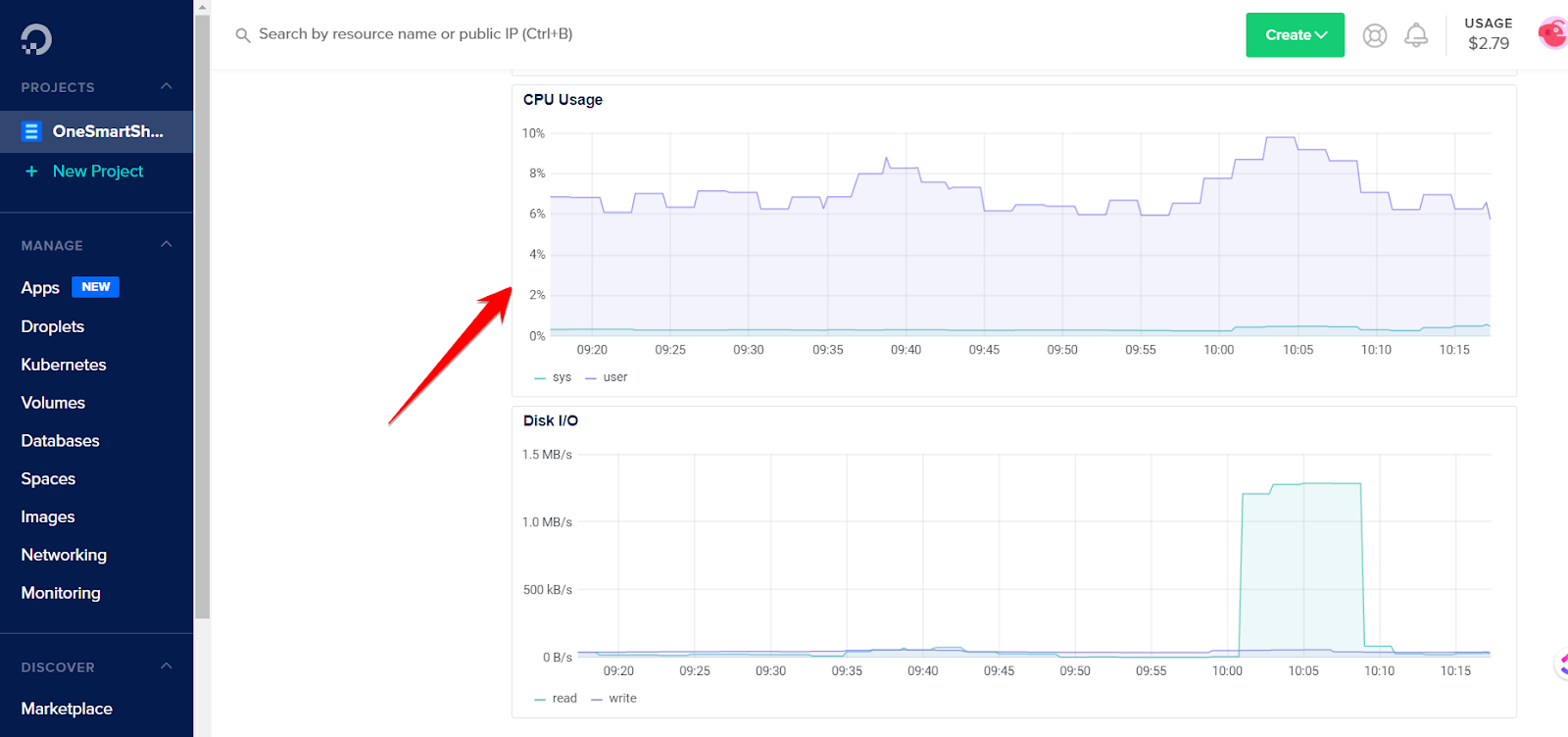
And when you log in to the terminal, it clearly shows how much RAM, CPU, and disk space is being consumed.

And if you want to see which processes are consuming the most resources, type top in the terminal (SSH), you’ll see this complicated box.
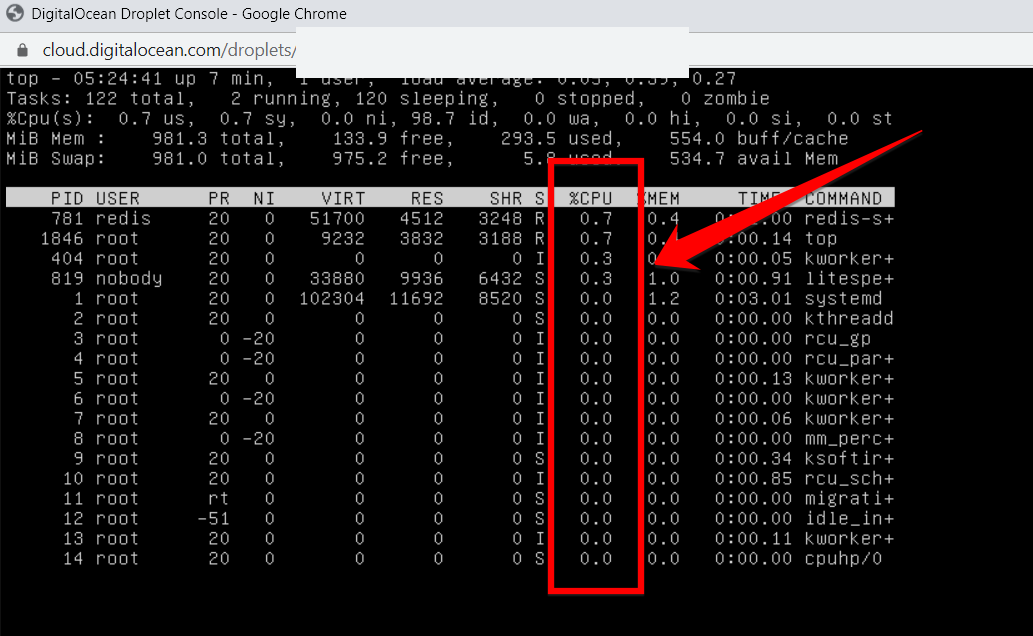
You can remove the process that is taking much of your CPU resources by typing the below line:kill -15 16330Change from 16330 to your PID of that process.
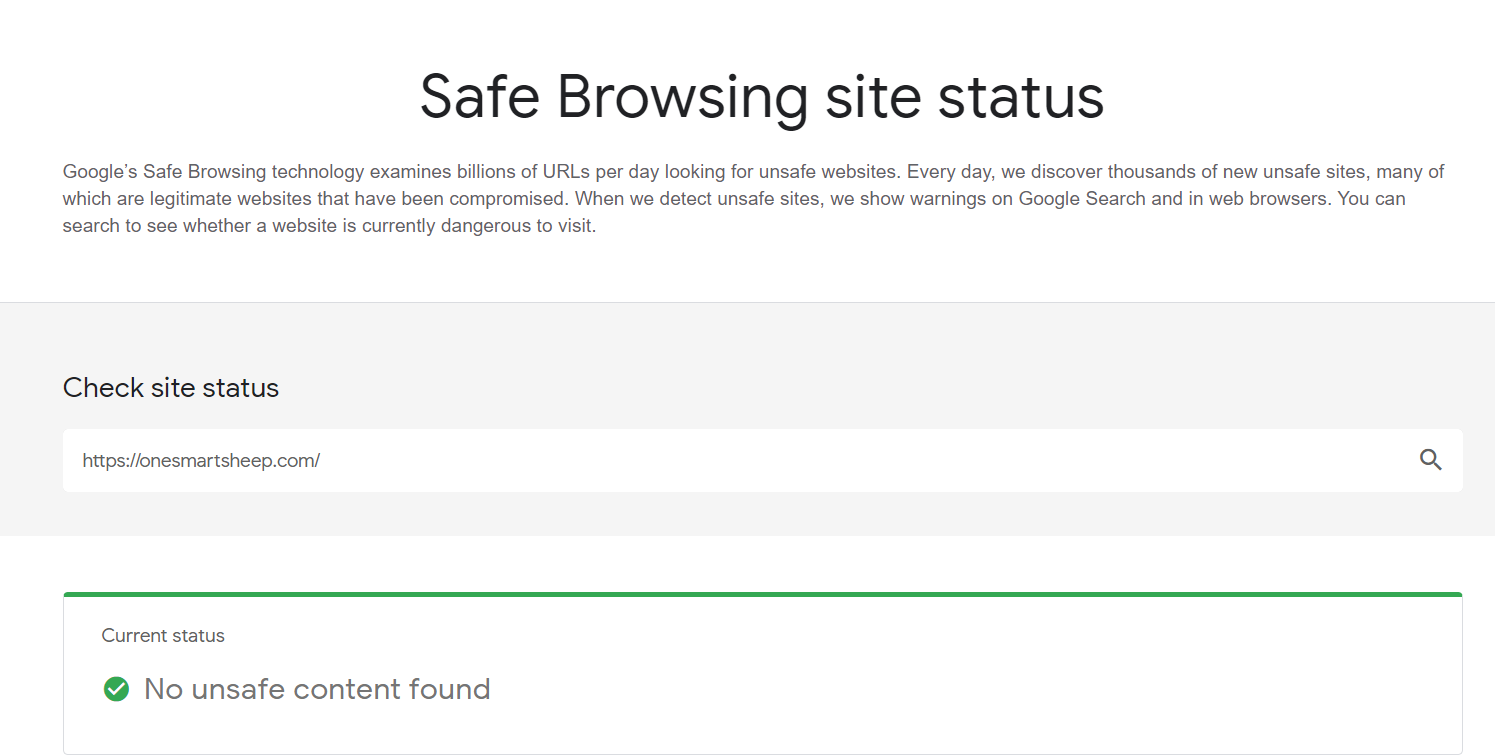
3. Use Google’s Safe Browsing tool.
Google’s Safe Browsing technology checks millions of URLs daily and hunts unsafe websites. To check your website, go to Safe Browsing site status, type your website to discover either it’s been hacked or not.
4. Check Search Results on Google
It’s the most potent tip that demonstrates how much hackers have damaged your site.Type site:yourwebsitename.com on Google.Typically, your website will look like this:
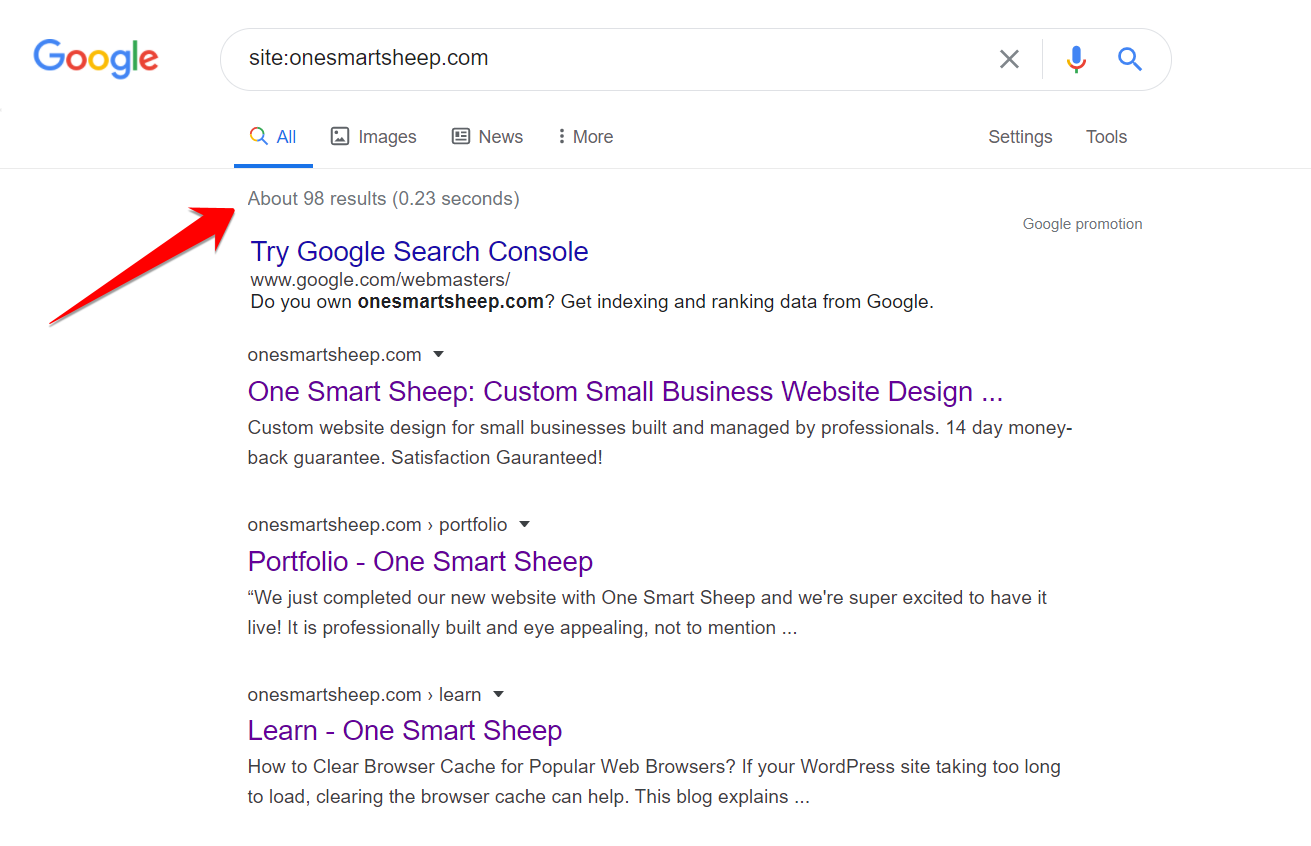
If it’s hacked, you’ll find the Japanese search results like this:
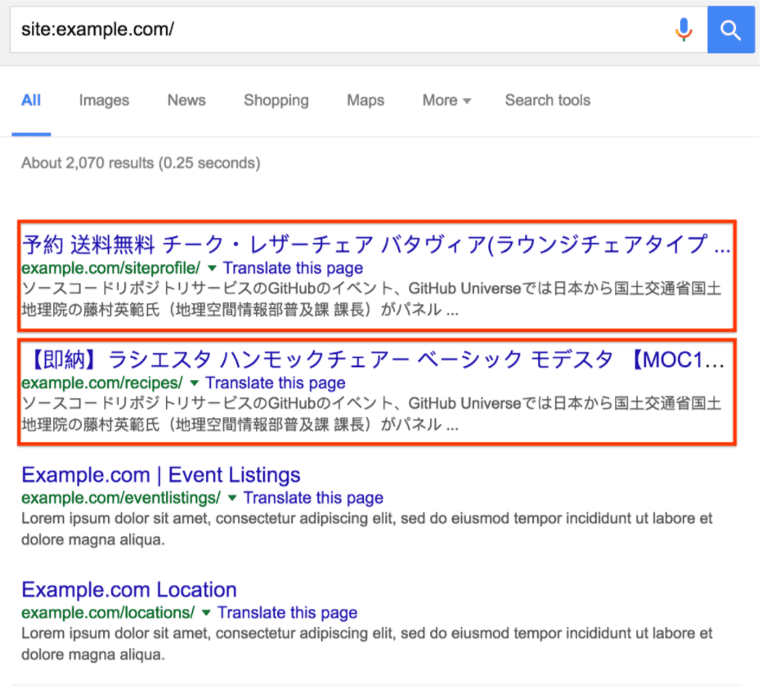
After reading the article, I’m sure you’ll be able to fix your hacked WordPress site in 80% of the cases. If you think you can’t do it, we at One Smart Sheep provide you with all the services related to WordPress development, maintenance, repairing, and hacking fix for a low cost.
5. Spam Ads
Are you noticing suspicious activities on your blog? It's highly likely your website has been hacked, and a hacker is trying to earn money through pop ads.Several ads companies don’t need manual approval, and hackers take advantage of such pop-up and notification ads to earn money.
A few hackers may also attempt to hack the site to place a backlink to rank their websites higher on Google, especially on the government and educational websites worth more in Google’s eyes.
How to Prevent WordPress Hacks?
It's essential to take measures to prevent your WordPress website from being hacked in the first place. Here are some steps you can take:
Choose a Secure Hosting Provider
Choosing a secure hosting provider is essential for ensuring the safety and security of your website. Look for a reputable provider that prioritizes website security and offers features like SSL certificates, regular backups, and malware scans.

You can also check online reviews and ratings to find a hosting provider with a good security track record.
Use Strong Passwords
Strong, unique passwords are crucial for protecting your website from hacking attempts. Use a combination of uppercase and lowercase letters, numbers, and symbols, and avoid using easily guessable words or phrases.
Weak Passwords:
- Passwordspassword
- Summer2022
Normal passwords
- P@ssw0rd!123123456<
- PurpleBanana3Tr0ub4dor&3qwerty
Additionally, avoid reusing passwords across multiple accounts to minimize the risk of a password leak.
Keep WordPress, Themes, and Plugins Updated
Keeping your WordPress core, themes, and plugins up to date is essential for protecting your website from security vulnerabilities. Hackers often exploit outdated software to gain access to websites, so make sure to install updates as soon as they become available.
You can check for updates from your WordPress dashboard or through your hosting provider's control panel.
Install Security Plugins
Security plugins are a great way to add an extra layer of protection to your WordPress website. Popular options include Wordfence, iThemes Security, and Sucuri.

These plugins offer features like firewall protection, malware scanning, and login security to help keep your website secure.
Remove Unused Plugins and Themes
Unused themes and plugins can pose a security risk, even if they're not actively being used on your website. Hackers can exploit vulnerabilities in outdated or inactive software, so make sure to delete any themes or plugins that you're not using.
This will reduce the attack surface of your website and make it harder for hackers to gain access.
Secure File Permissions
File permissions determine who can access files on your server, so it's important to make sure they're set to the appropriate level. Generally, files should be set to 644 and directories to 755. This will prevent unauthorized access and help keep your website secure.
Enable Two-Factor Authentication
Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of identification in addition to your password. This can be a code sent to your phone or a biometric factor like a fingerprint. Enabling two-factor authentication for all accounts associated with your website, including FTP accounts, hosting accounts, and WordPress admin accounts can help prevent unauthorized access even if a hacker gains access to your password.
Backup Regularly
Regular backups are an essential part of website security. They allow you to restore your website to a previous state if it's hacked or if there is a problem with an update. There are several ways to back up your WordPress website, including:
- Manual backups: This involves manually copying your WordPress files and database to an external storage device. However, this can be time-consuming, and there's a risk of losing some data if you forget to back up certain files.
- Backup plugins: Many backup plugins are available for WordPress that automates the backup process. They allow you to schedule regular backups and store them in a secure location, such as an external storage device or cloud storage. Some popular backup plugins for WordPress include UpdraftPlus, VaultPress, and BackupBuddy.
- Managed WordPress hosting: Some WordPress hosting providers offer managed hosting plans that include regular backups as part of the service. This is a good option if you want to avoid managing backups yourself.
Whichever backup method you choose, it's important to test your backups regularly to ensure they are working correctly.
Limit Login Attempts
Limiting login attempts can protect your website from brute force attacks, where a hacker tries to guess your username and password by repeatedly attempting to log in. You can limit login attempts using a plugin, such as Login LockDown, which allows you to set a limit on the number of login attempts from an IP address.Once the limit is reached, the plugin will block further login attempts from that IP address for a specified amount of time. This makes it difficult for hackers to guess your login credentials and gain access to your website.However, it's important to note that limiting login attempts can also lock out legitimate users if they mistype their login credentials too many times. So, it's a good idea to balance security with usability by setting a reasonable limit on login attempts.
Let Us Protect Your WordPress Site For a Lifetime
One Smart Sheep doesn’t only fix hacked WordPress but also builds custom websites, hosts, markets, and maintains for an affordable price. You don’t need to worry about your WordPress site ever. You’ll focus on running your business and we keep your WordPress website healthy, safe, & secure.
Frequently Asked Questions
Does WordPress get hacked?
Yes, WordPress websites can get hacked. As the most widely used content management system (CMS), WordPress is often targeted by hackers due to its popularity. However, it's important to note that WordPress itself is a secure platform. Most hacks occur due to vulnerabilities introduced by outdated core software, themes, plugins, or weak login credentials.
How often is WordPress hacked?
The frequency of WordPress hacks varies, but it's a common occurrence. According to a report by Sucuri, a website security company, WordPress websites accounted for 90% of all CMSs infected with malware in 2018. However, this high percentage is primarily due to WordPress's market share dominance. Regular updates, strong passwords, and proper security measures can significantly reduce the risk of hacking.
Which steps should you take if your WordPress site is hacked?
If your WordPress site is hacked, you should take the following steps:
- Immediately change all login passwords, including WordPress admin, FTP, and hosting control panel.
- Inform your hosting provider about the hack and request their assistance.
- Back up your website files and database, even if they're compromised.
- Identify and remove the vulnerability that allowed the hack to occur.
- Clean up the hacked files and database, or restore a clean backup.
- Update all WordPress core files, themes, and plugins to their latest versions.
- Run a thorough malware scan using a reputable security plugin or service.
- Implement security measures such as two-factor authentication, firewall protection, and regular monitoring.
Is WordPress the most hacked CMS?
While WordPress is the most widely used CMS and often tops the list of the most hacked CMSs, it's not necessarily the most vulnerable. The high number of hacks is primarily due to its popularity and the fact that many users fail to implement proper security measures or keep their installations up to date. Other CMSs like Joomla and Drupal also face similar security challenges. Ultimately, the security of a website depends more on how it's maintained and secured, rather than the specific CMS it uses.
















.svg)